The following steps are specific to the Custom SAML application and are required in order to enable SSO for Custom SAML.
To add and configure a Custom SAML application
1.In Admin Portal, click Apps, then click Add Web Apps.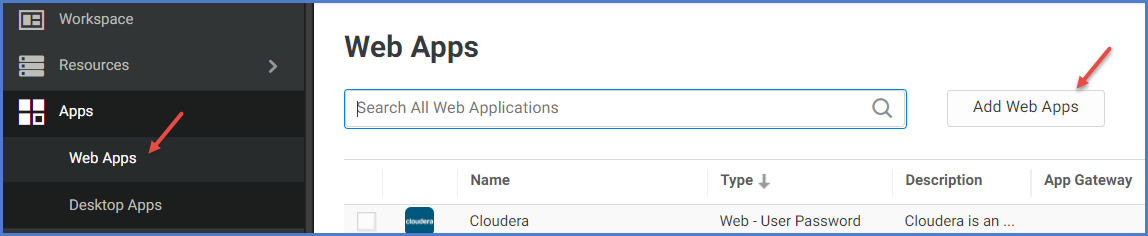
The Add Web Apps screen appears.
2. Click Custom.
3. On the Custom tab, next to the SAML application click Add.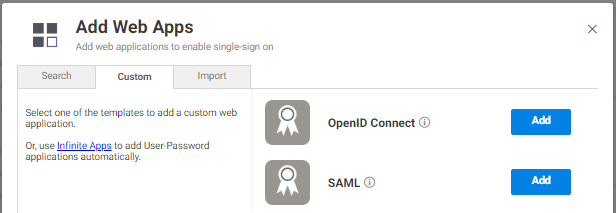 4. In the Add Web App screen, click Yes to add the application.
4. In the Add Web App screen, click Yes to add the application.
Admin Portal adds the application.
5. Click Close to exit the Application Catalog.
The application that you just added opens to the Settings page.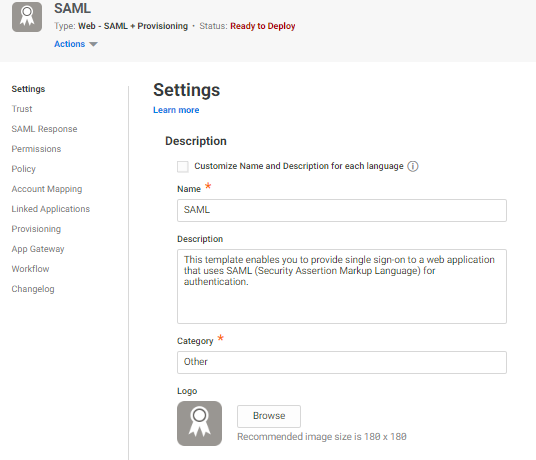
6. Name the App and click save.
7. Click Trust to go to the Trust page.
The Trust page contains fields and controls for SAML information that might be required by the web application Service Provider. You must supply this information in the format requested by the Service Provider.
The Trust page is divided into two parts:
- Identity Provider Configuration
- Service Provider Configuration
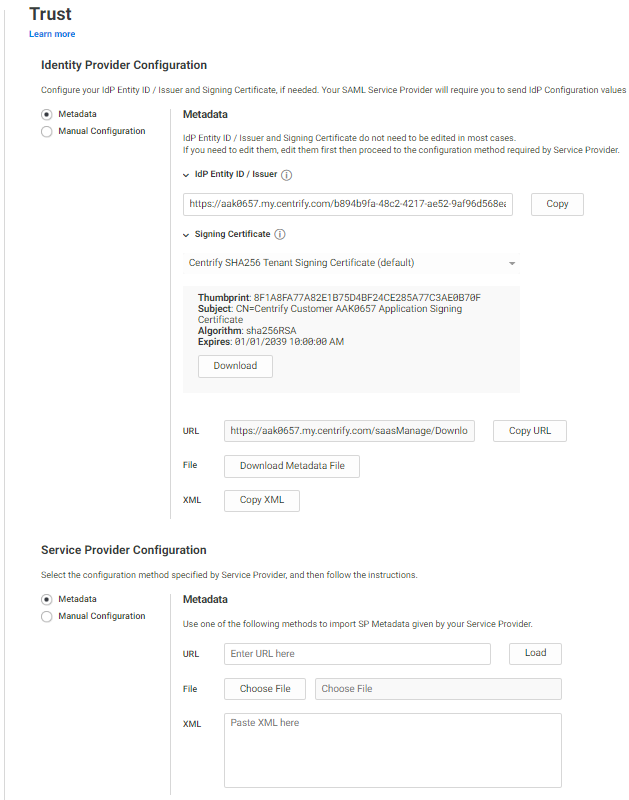
The next steps provide the information about the SAML information available on the Trust page, broken down by section for both Metadata and Manual Configuration.
8. Update the information for the Identify Provider Configuration section, the click Save.
The only change that might be required in the identity Provider Configuration section is changing the signing certificate.
|
Option |
Description |
|
Identify Provider Configuration |
|
|
Metadata (selected) |
|
|
IdP Entity ID / Issuer |
The IdP Entity ID can also be referred to as an Issuer. A URL unique to this application profile. This value is the entity ID used in the SAML assertion to identify the identity provider attempting to authenticate. The web application doesn’t contact this URL so it need not be functional. |
|
Signing Certificate |
These settings specify the signing certificate used for secure SSO authentication between the Centrify Privileged Access Service and the web application. Just be sure to use a matching certificate both in the application settings in the Admin Portal and in the application itself. Select an option to change the signing certificate. Use the Default Tenant Application Certificate (default) Select this option to use the Centrify Privileged Access Service standard certificate. This is the default setting. Click Download to save the certificate so you can use it during the application configuration process. If you replace the certificate, be sure to update application with the new certificate information. -Upload New Signing Certificate- Select this option to upload your organization’s own certificate. To use your own certificate, you must enter a name and a password (if the file requires a password) and then click Browse to upload an archive file (.p12 or .pfx extension) that contains the certificate along with its private key. Upload the certificate from your local storage prior to downloading any IdP metadata. If the IdP metadata is available from a URL, be sure to upload the certificate prior to providing the URL to your service provider. |
|
URL |
The information for the certificate that you have selected is shown in the URL field. Click Copy URL to easily copy the address of the certificate. Use this URL to configure your SAML application (this is similar to downloading the metadata and sending it to the service provider but instead you just provide the URL). This method can be used as an alternative to downloading the metadata. The method used depends on service provider requirements. |
|
File |
Click Download Metadata File to download SAML metadata in an XML file. The metadata contains the security certificate and other SAML information that you can provide to the service provider. For Business Partner Federation, this is the information that you need to provide to the service provider/host. |
|
XML |
Click Copy XML to copy the XML content. This is similar to downloading the metadata and sending it to the service provider but instead you just provide the XML content. This method can be used as an alternative to downloading the metadata. The method used depends on service provider requirements. |
|
Option |
Description |
|
Identify Provider Configuration |
|
|
Manual Configuration (selected) |
|
|
IdP Entity ID / Issuer |
The IdP Entity ID can also be referred to as an Issuer. A URL unique to this application profile. This value is the entity ID used in the SAML assertion to identify the identity provider attempting to authenticate. The web application doesn’t contact this URL so it need not be functional. |
|
Signing Certificate |
These settings specify the signing certificate used for secure SSO authentication between the Centrify Privileged Access Service and the web application. Just be sure to use a matching certificate both in the application settings in the Admin Portal and in the application itself. Select an option to change the signing certificate.
|
|
Single Sign On URL |
The URL that the service provider uses to notify the Centrify Privileged Access Service of SAML Single Sign On. |
|
Single Logout URL |
The URL the service provider uses to notify the IdP of SAML Single Logout. |
|
Single Sign On Error URL |
The URL that the service provider uses to notify the Centrify Privileged Access Service if there’s a SAML Single Sign On Error. |
9. Complete the information for the Service Provider Configuration section by uploading metadata provider by your service provider or by using the manual configuration, then click Save.
|
Option |
Description |
|
Service Provider Configuration |
|
|
Metadata (selected) |
|
|
URL |
If your SAML application vendor supplies you with an SP Metadata URL, enter the URL in the input field and then click Load. |
|
File |
If your SAML application vendor supplies you with an SP Metadata File, click Choose File, select the file. The file name appears in the Choose File field. |
|
XML |
If your SAML application vendor supplies you with SP Metadata XML content, copy it and place it in the Paste XML here input field. |
|
Option |
Description |
|
Service Provider Configuration |
|
|
Manual Configuration (selected) |
|
|
SP Entity ID/ Issuer /Audience |
Enter the Entity ID that your SAML application vendor supplies. This Entity ID is also known as Service Provider Issuer or Audience. |
|
Assertion Consumer Service (ACS) URL |
The Assertion Consumer Service (ACS) URL specifies the URL to which the Centrify Privileged Access Service sends the SAML response. The ACS URL is provided by the application vendor (service provider). Enter the ACS URL provided by the application vendor. |
|
Recipient Same as ACS URL |
Only uncheck the checkbox and enter the Recipient value when the Service Provider instructs you to do so. |
|
Sign Response or Assertion? |
The Service Provider will specify the Response or Assertion to be signed. Click the applicable button. |
|
<NameID> Format |
The Service Provider will specify the NameID format to use. If unknown, leave the format as unspecified. |
|
Encrypt SAML Response Assertion |
If a Service Provider supports this feature, and you want to use it, check the check box first. Click the Choose File button to select the Public Certificate that the Service Provider sends to you. The Subject Name and Thumbprint information is shown after the Public Certificate has been selected. |
|
Relay State |
If the Service Provider specifies a Relay State to use, enter it in the input field. |
|
Authentication Context Class |
If the Service Provider specifies the Authentication Context Class to use, select the applicable option. If unknown, leave the option as unspecified. |
10. Click Save to preserve your changes.
11. On the SAML Response page, use the Attributes section to Configure the SAML attributes according to the Service Provider requirements.
In the Custom Logic section, use the Editing the assertion script if you require more complex logic for attribute mappings for your SAML Response.
12. (Optional) If you want to easily identify your Custom SAML app, customize the Logo on the Settings page for your app.
This alphabetizes your app under the name you give it and provides the visual cue of your custom logo.
