Purpose
This article explains how to prevent browser from remembering credentials via Microsoft Endpoint Manager (Intune).
Prerequisites
- Office 365 Global Administrator
- Endpoint Manager Licensed and Deployed
Instructions – Create Policy
- Login to Office 365 Admin Center. https://admin.microsoft.com/Adminportal
- Go to Endpoint Manager.
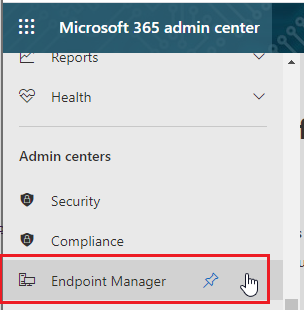
- Click on Devices.
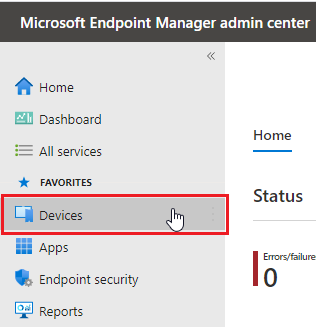
- Go to Configuration Profiles.
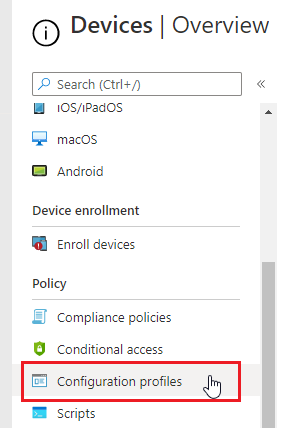
- Click on Create Profile.
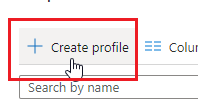
- Continue below for the browsers required. You will need to create a Profile for each browser you want to block.
Microsoft Edge
- Configure the following and click Create. Platform “Windows 10 and Later”, Profile Type “Templates”, Template name “Administrative Templates”.
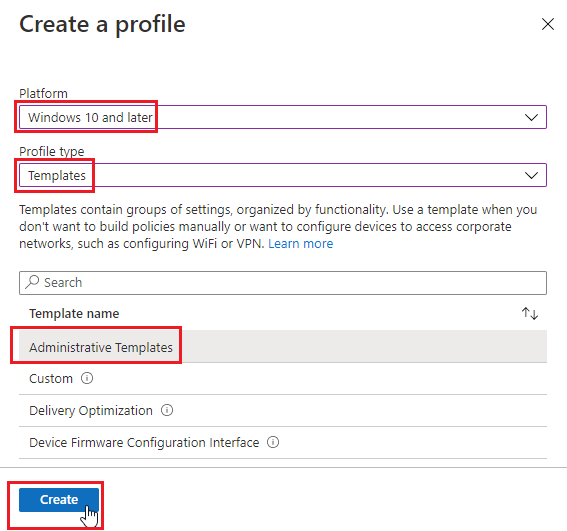
- Name the Profile “Deploy Practice Protect Plugin Microsoft Edge” and click Next.
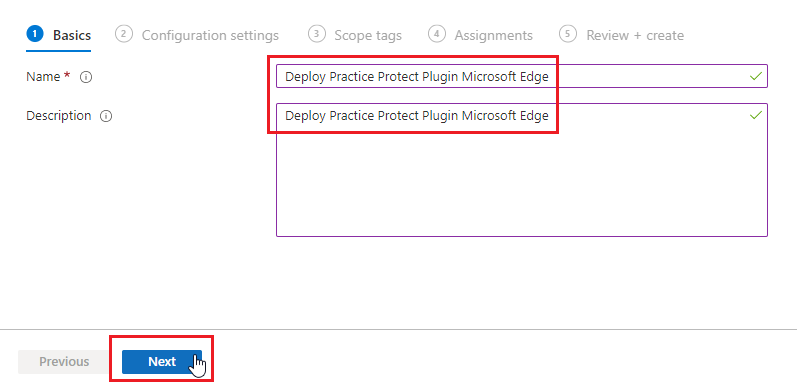
- In the search box type “Control which extensions are installed silently” then select the one that does not include “users can override” the click on it to Configure it.

- Set Enabled and use the following extension URL: mblkikdcdlfpljlmgijhccbhiijkhded;https://edge.microsoft.com/extensionwebstorebase/v1/crx then click Ok.
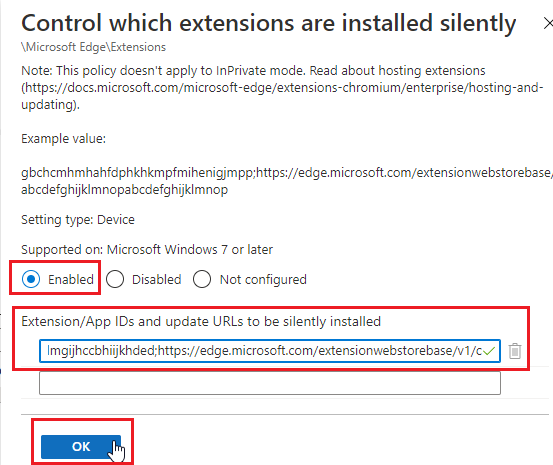
- Click Next.
- Leave scope as Default and click Next.
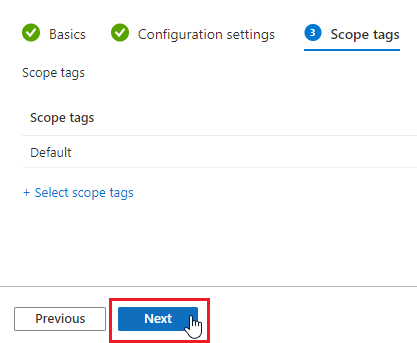
- Select All Users and All Devices (You may use custom groups as well). Click Next.
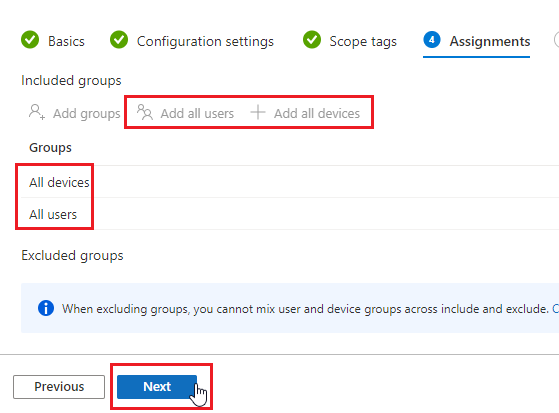
- Confirm the configuration and click Next.

- The policy will now deploy out to devices when they next check-in.
- Continue below for Chrome and Firefox Polices.
Google Chrome
- Configure the following and click Create. Platform “Windows 10 and Later”, Profile Type “Settings catalog”.

- Name the Profile “Deploy Practice Protect Plugin Google Chrome” and click Next.

- Click “+ Add settings”.

- Type “silently installed (Device)“, select “Administrative Template\ Google\ Google Chrome\ Extensions” and tick the box next to “Extension/App IDs and update URLs to be silently installed (Device)”

- On the left side of the window, click “Enable” next to “Configure the list of force-installed apps and extensions” and past the next text (jifcoadedkediabkmjbflemiblmnbjfk;https://clients2.google.com/service/update2/crx) to the empty row as it shows on the picture.

- Leave scope as Default and click Next.

- Select All Users and All Devices (You may use custom groups as well). Click Next.

- Confirm the configuration and click Next.

- The policy will now deploy out to devices when they next check-in.
- Continue below for Firefox Polices.
Mozilla Firefox
- Download updated FireFox ADMX file from https://support.practiceprotect.com/downloads/firefox_updated.admx
- Go back in End Point Manage. Click Create Profile.

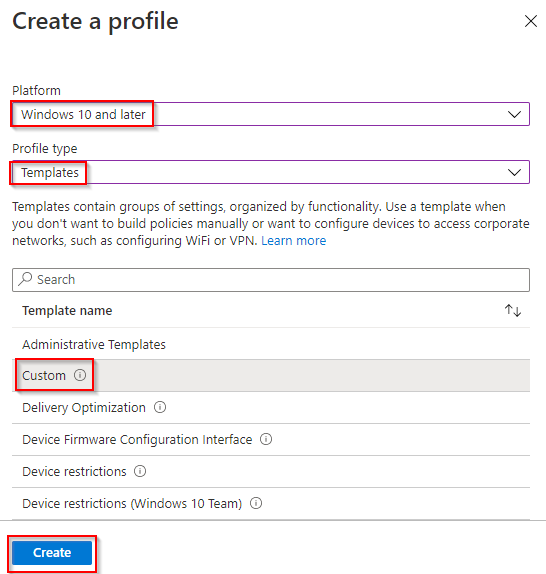
- Configure the following and click Create. Platform “Windows 10 and Later”, Profile Type “Templates”, Template name “Custom”.
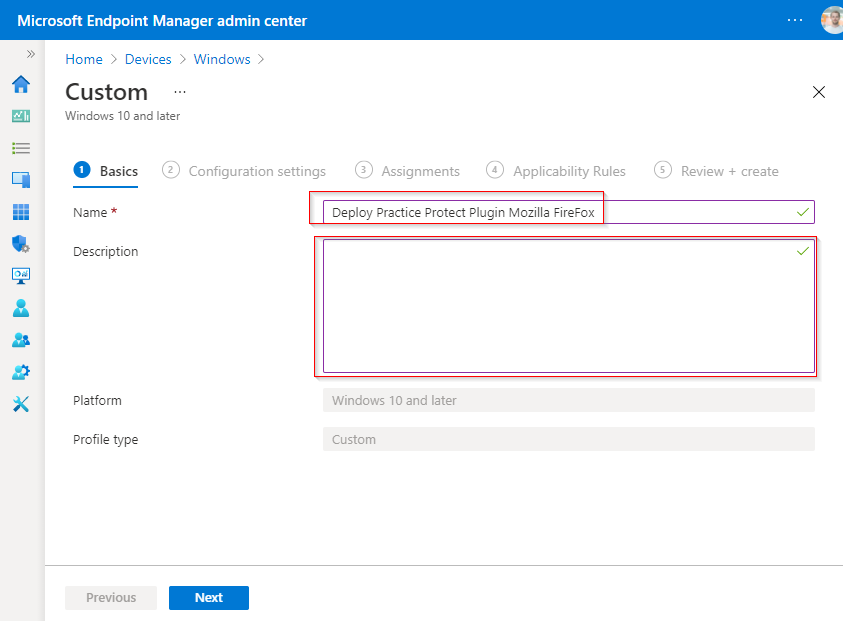
- Fill out fields below and type “Deploy Practice Protect Plugin Mozilla Firefox” in the Name field then click Next
- Click Add to add a new OMA-URI.
- Fill Up all fileds.
- Set Name to “Firefox ADMX”
- “OMA-URI” to “./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/FirefoxAdmx“
- Copy content from the file firefox_updated.admx to the “Value” field
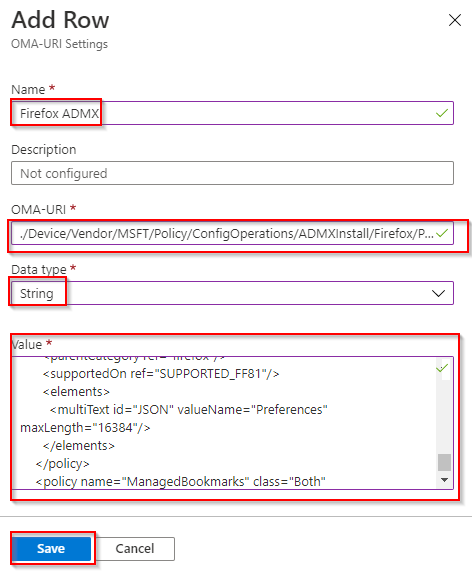 click Save.
click Save.
- Click Add again.
- Fill Up all fileds.
- Set Name to “Extensions_Install“
- OMA-URI to “./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox~Extensions/Extensions_Install“
- Data type “String“
- Value to “<enabled/>
<data id=”Extensions” value=”1https://addons.mozilla.org/firefox/downloads/file/4110179/cyberark_identity_browser-23.5.4.xpi”/>”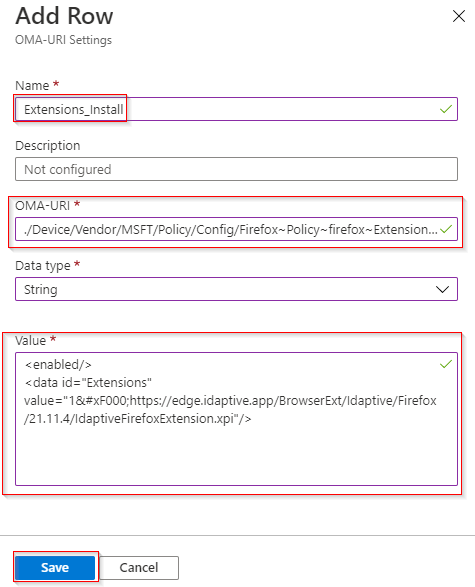 and click Save.
and click Save.
- Click Add again.

- Fill Up all fileds.
- Name = Extensions_Locked
- OMA-URI = “./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox~Extensions/Extensions_Locked“
- Data type to “String“
- Value to “<enabled/>
<data id=”Extensions” value=”1IdaptiveBrowserExtension@idaptive.com”/>”

- Click Next.

- Select All Users and All Devices (You may use custom groups as well). Click Next

- Confirm the configuration and click Next.

- The policy will now be deployed to devices when they check-in next time.
- In case you are using Intune to disable “Password Manager”, you will need to use “firefox_updated.admx” file from this guide to avoid conflict.
