Purpose
This article explains how to prevent browser from remembering credentials via Microsoft Intune.
Prerequisites
- Microsoft 365 Account with Global Administrator or Intune Administrator role
-
Microsoft Intune Plan 1 license or a comparable Microsoft 365 plan that includes Intune capabilities, such as Microsoft 365 E3, E5, or Business Premium, is required. Note that Microsoft Entra ID Plan 1 does not include Intune capabilities.
Instructions
- Sign in to the Microsoft Intune Admin Center

- In the left menu, click on Devices and then click on Configuration under Manage devices
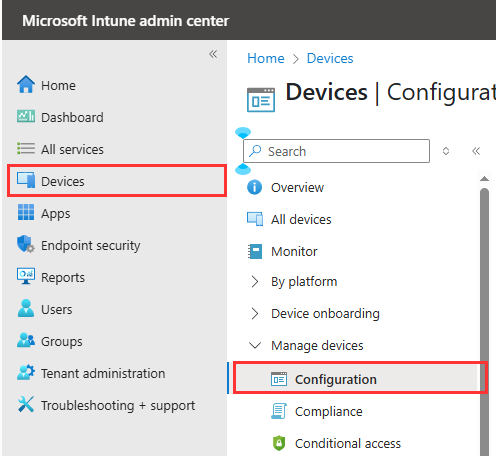
- On the Policy tab, click Create and select New Policy
- Continue with the steps below for each required browser. You’ll need to create a separate policy or profile for every browser you intend to block.
Microsoft Edge
- Configure the following and click Create. Platform “Windows 10 and Later”, Profile Type “Templates”, Template name “Administrative Templates”.
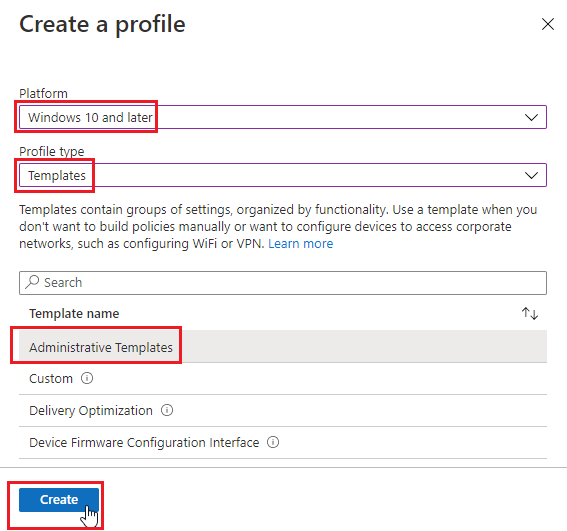
- Name the Profile “Block Password Saving Microsoft Edge” and click Next.
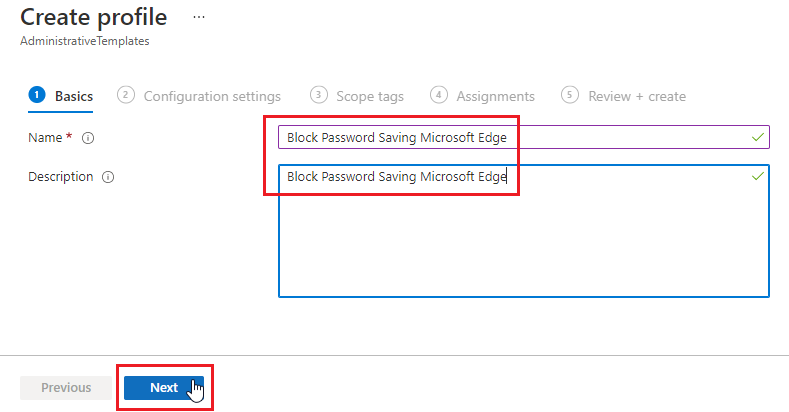
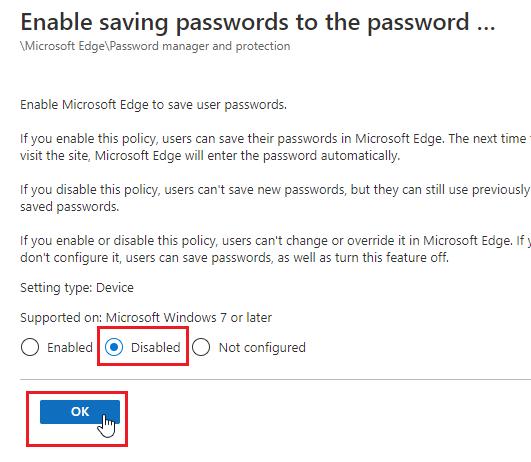
- In the search box type “Enable saving passwords to the password manager” then select the one that does not include “users can override” the click Next.
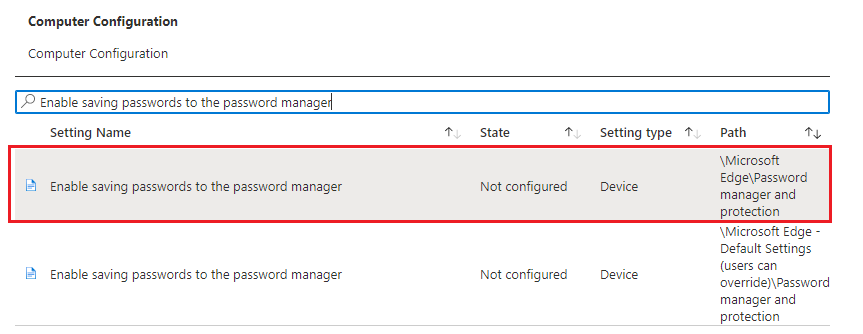
- Chose Disabled and Click Ok.
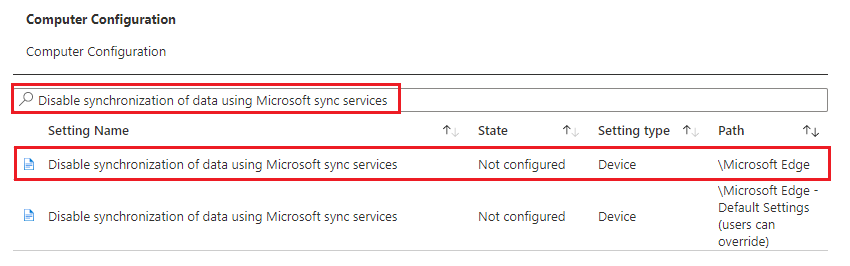
- In the search box type “Disable synchronization of data using Microsoft sync services” then select the one that does not include “users can override” the click Next.
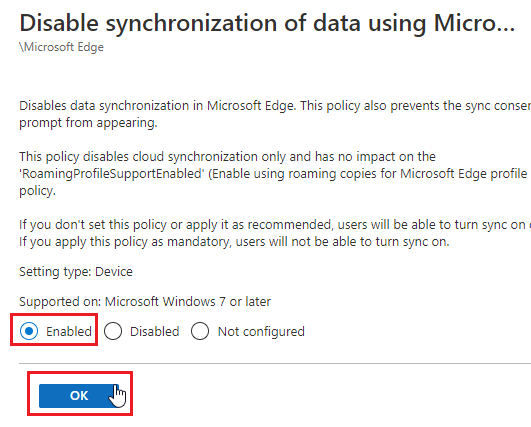
- Chose Enabled and Click Ok.
- Click Next.
- Leave scope as Default and click Next.
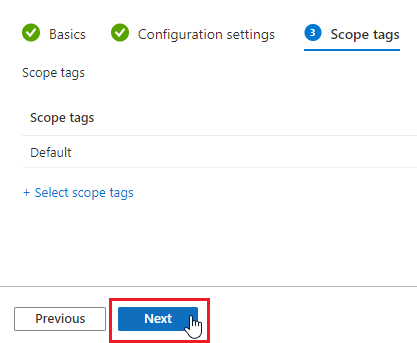
- Select All Users and All Devices (You may use custom groups as well). Click Next.
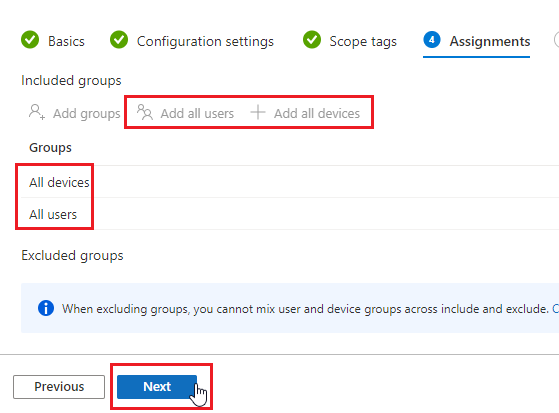
- Confirm the configuration and click Next.
- The policy will now deploy out to devices when they next check-in.
- Continue below for Chrome and Firefox Polices.
Google Chrome
- Click Create Profile
- Configure the following and click Create. Platform “Windows 10 and Later“, Profile Type “Settings catalog“
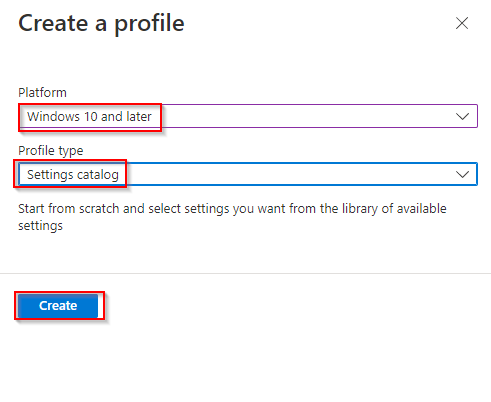
- Name and Description “Block Password Saving Google Chrome” and click Next
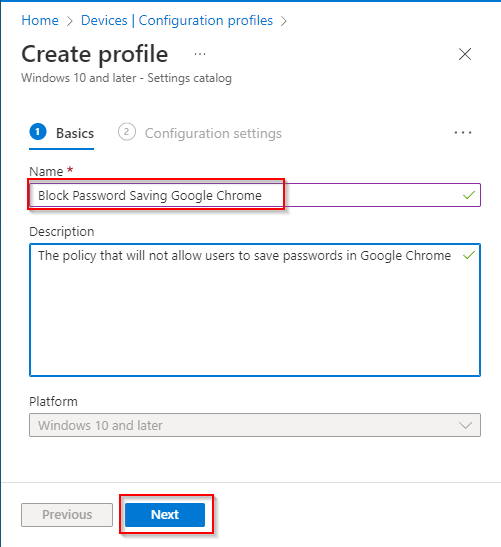
- Click “Add settings”
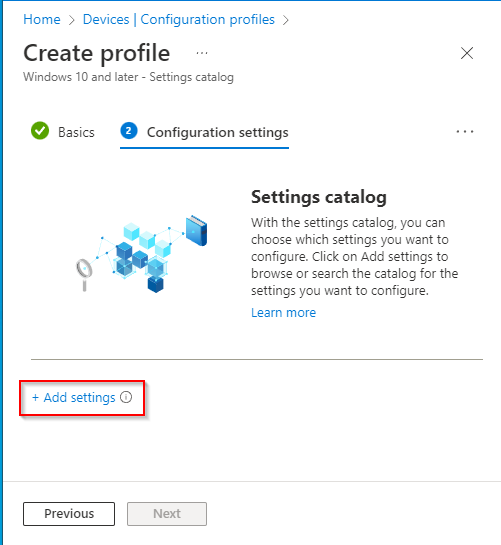
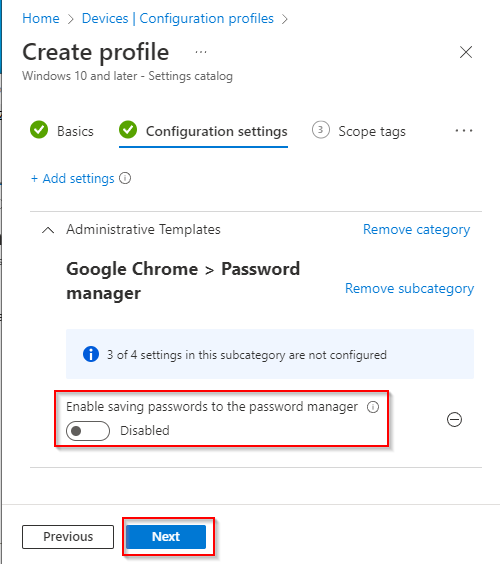
- Type “google” in “Search” and select “Administrative Templates\ Google\ Google Chrome\ Password manager“. Then tick the box “Enable saving passwords to the password manager”
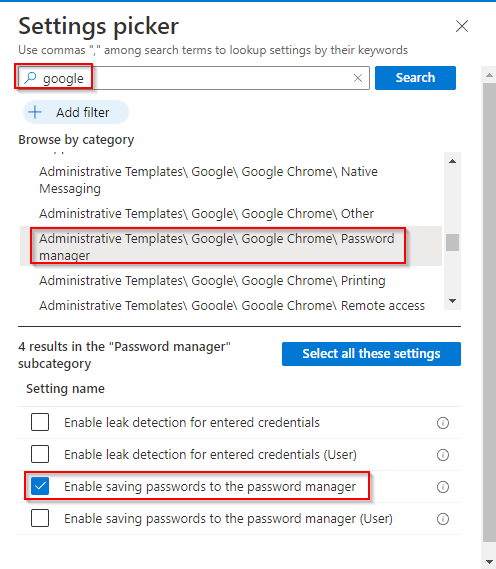
- Make sure that the policy is set to “Disabled” as it showed in the screenshot below and click “Next“.
- Click “Add all users” under Included groups to deploy the policy to all users.
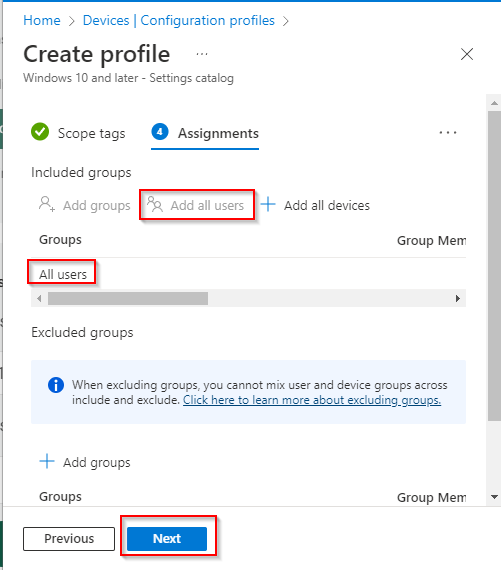
- Click “Next” and “Create” to finish
- Continue below for Firefox Polices.
Mozilla Firefox
- Download FireFox Polices from: https://github.com/mozilla/policy-templates/releases
- Under Assets, Click policy_templates.zip to Download.
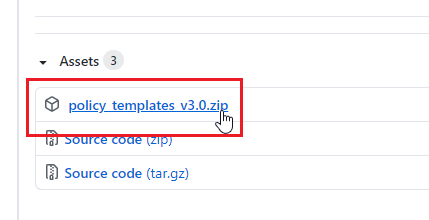
- Unzip/Extract the downloaded Zip File.
- Open the extracted folder and Go to policy_templates_v3.0\windows and look for firefox.admx
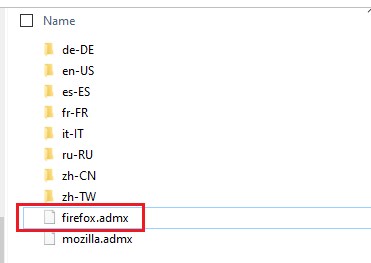
- Right Click on FireFox.admx and click Open with.
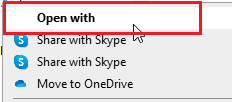
- Chose Notepad and unselect Always Use and click Ok.
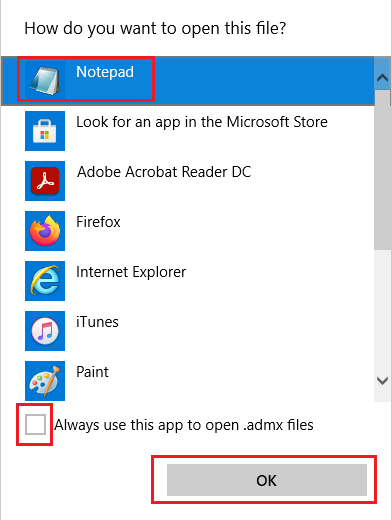
- Ctrl+A to select everything and Right-Click and Copy. This will be needed in step 11
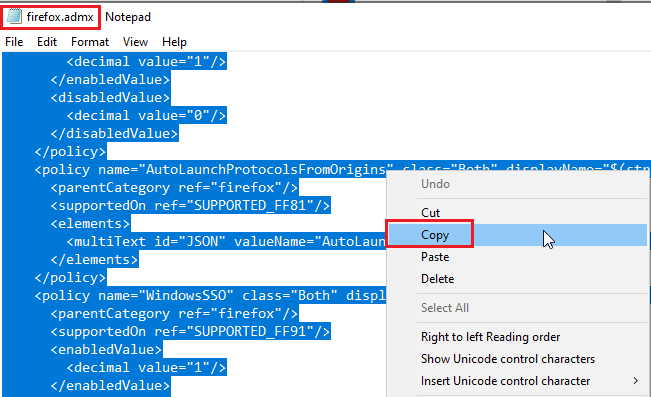
- Back in End Point Manage. Click Create Profile.

- Configure the following and click Create. Platform “Windows 10 and Later”, Profile Type “Templates”, Template name “Custom”.
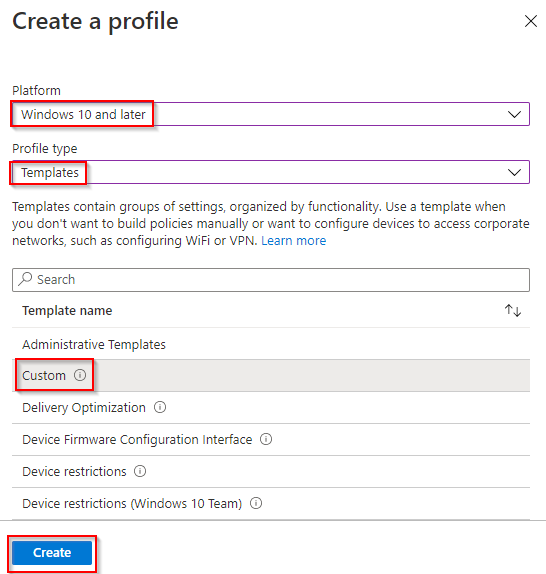
- Name and Description “Block Password Saving Mozilla FireFox” and click Next.
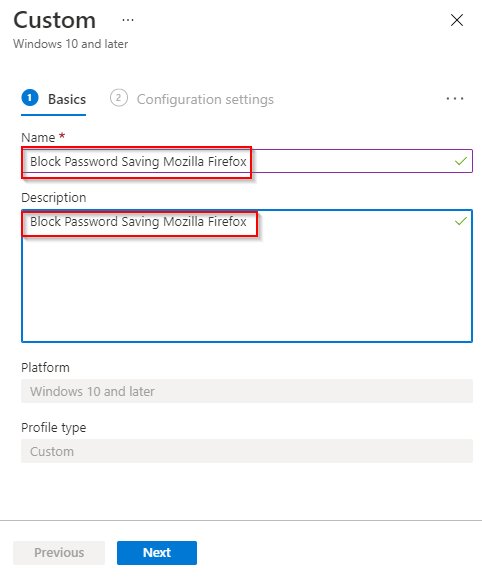
- Click Add.
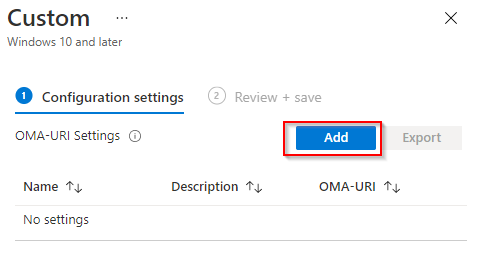
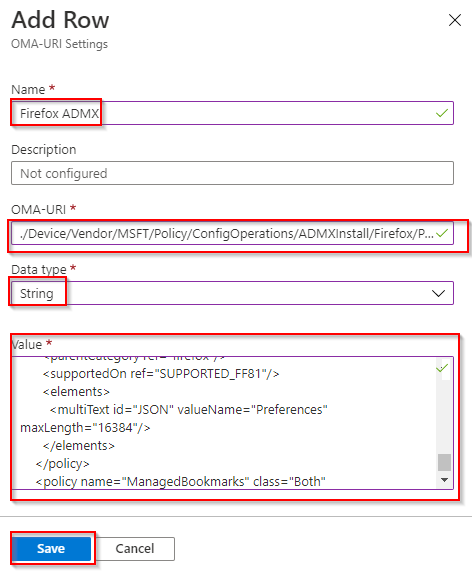
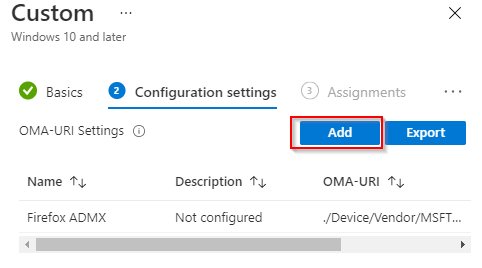
- Configure the following and click Save. Name: “FireFox ADMX ” OMA-URI: “./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/FirefoxAdmx” Datatype: “String” Value: “Contents of Step 7” then click Save.
- Click Add again.
- Configure the following and click Save. Name: “PasswordManagerEnabled” OMA-URI: “./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/PasswordManagerEnabled” Datatype: “String” Value: “<disabled/>” then click Save.
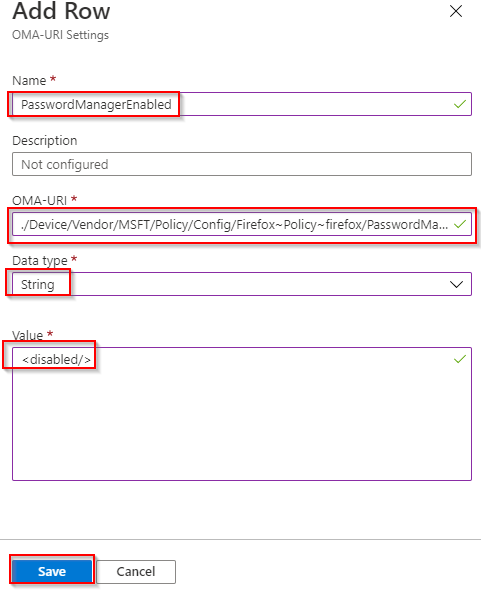
- Click Add again.

- Configure the following and click Save. Name: “DisbaleFireFoxAccounts” OMA-URI: “./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/DisableFirefoxAccounts” Datatype: “String” Value: “<enabled/>” then click Save.
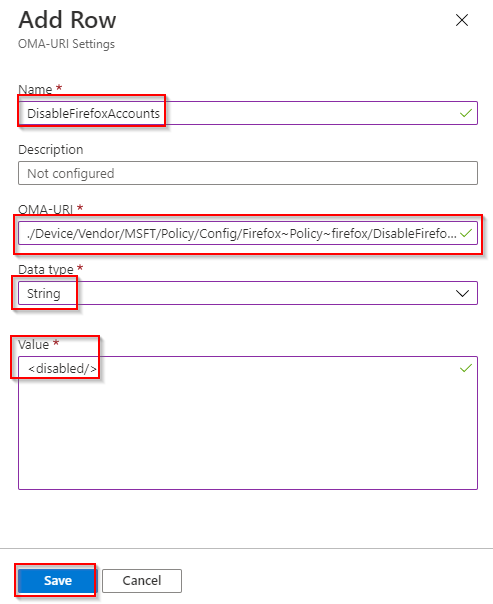
- Click Add again

- Configure the following and click Save. Name: “OfferToSaveLogins” OMA-URI: “./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/OfferToSaveLogins” Datatype: “String” Value: “<disabled/>” then click Save.
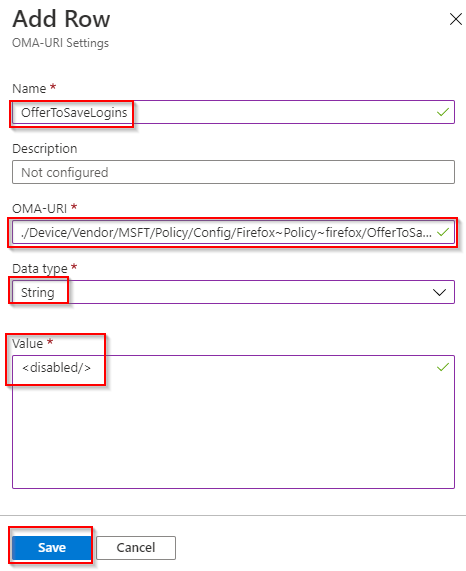
- Click Next.

- Select All Users and All Devices (You may use custom groups as well). Click Next

- Confirm the configuration and click Next.
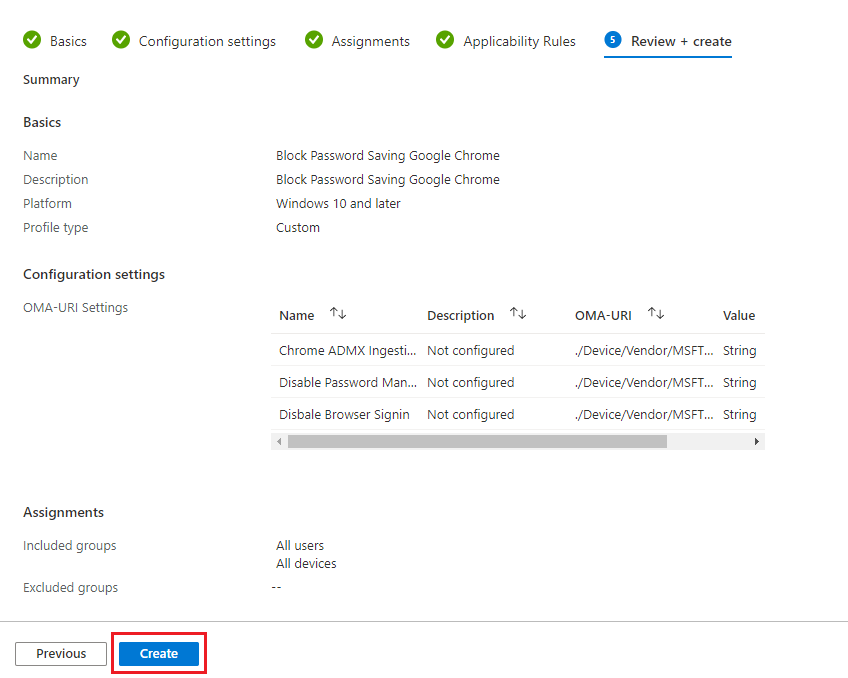
- The policy will now deploy out to devices when they next check-in.
- Finished
