Purpose
Slack offers single sign-on via SAML integration with Practice Protect. This provides a seamless login experience to the Slack platform using IdP-initiated SAML.
It can be useful to open the web application and Admin Portal simultaneously and have them both open, perhaps side by side. As part of the SSO configuration process, you’ll need to copy and paste settings between the two browser windows.
Practice Protect will configure this on your behalf. Please send us an email at support@practiceprotect.com
Pre-requisites
- Administrator Access in Practice Protect
- Active Slack account with administrator rights for your organization (Note: this can be your account so you don’t have to pay and create for another license account)
- A signed certificate. You can either download one from Admin Portal or use your organization’s trusted certificate.
- Must be on either Slack Business Plus or Enterprise Grid Subscription only
- Username/Email for staff should match the login names in Practice Protect.
Instruction
- Login to Practice Protect and switch to Admin portal.
- On Core Services, Click on Roles > Add Roles. Create a role and set the name field to “Slack SSO Users“. Then Save.
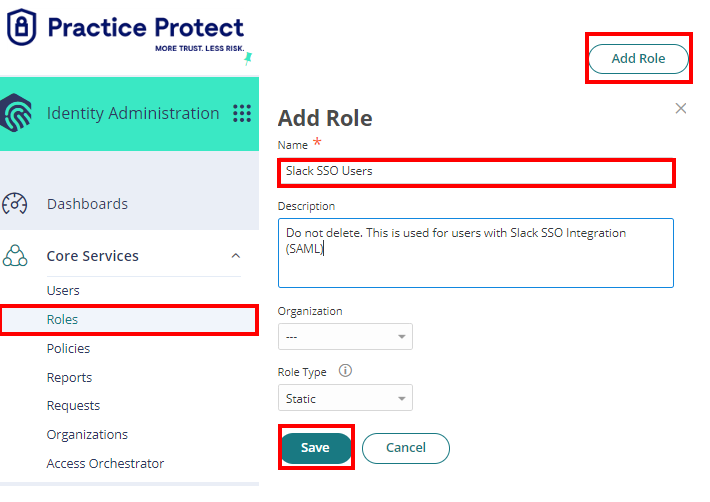
You can also create roles according to the group membership in Slack (Marketing, Administrator, Design, etc.)
- With the created role, click on Members > Add. Add each member/user that will be part of the SSO. Then Save.
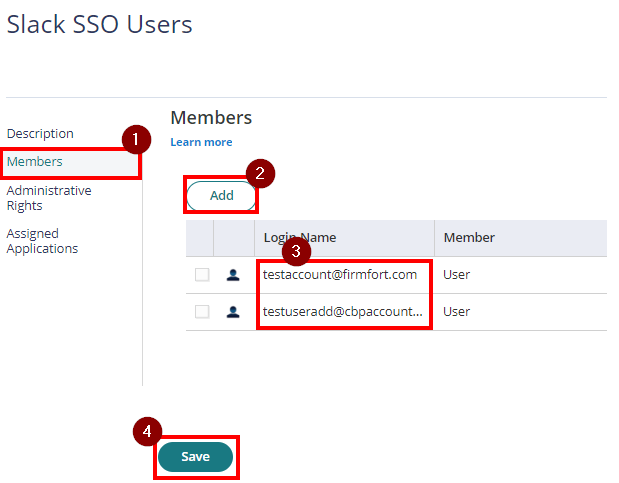
If you have multiple Groups you may create these groups accordingly and repeat steps 2-3. - From the Apps & Widgets, go to Web Apps section. Then, choose Add Web Apps on the top right corner.
On the app catalog, search for “Slack” and Add the app Slack Web – SAML + Provisioning”. Hit “Yes” to add the application. Click Close.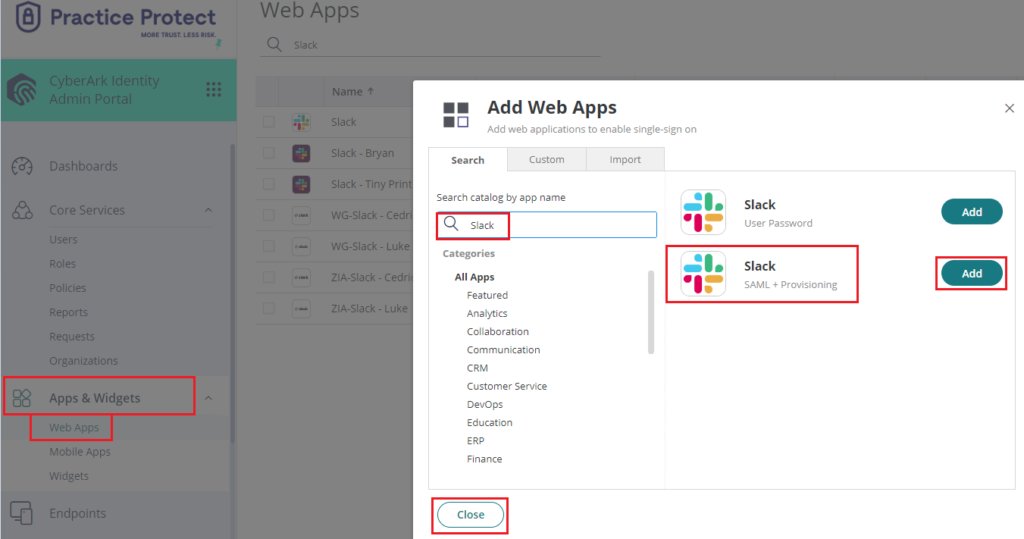
- The application that you just added opens to the Settings page. Set the Name to “Slack SSO” then click Save. Note: You can change the name, category or logo based on your preference.
- Click on Trust > On Identity Provider Configuration select Manual Configuration > Click on Signing Certificate and click Download.
This will download the certificate on your local PC which you will need on the succeeding instructions. Copy the Identity Provider Issuer and SAML 2.0 Endpoint (HTTP) on a notepad.
You will also need this details on the succeeding instructions. On Service Provider Configuration, select Manual Configuration then click
Save.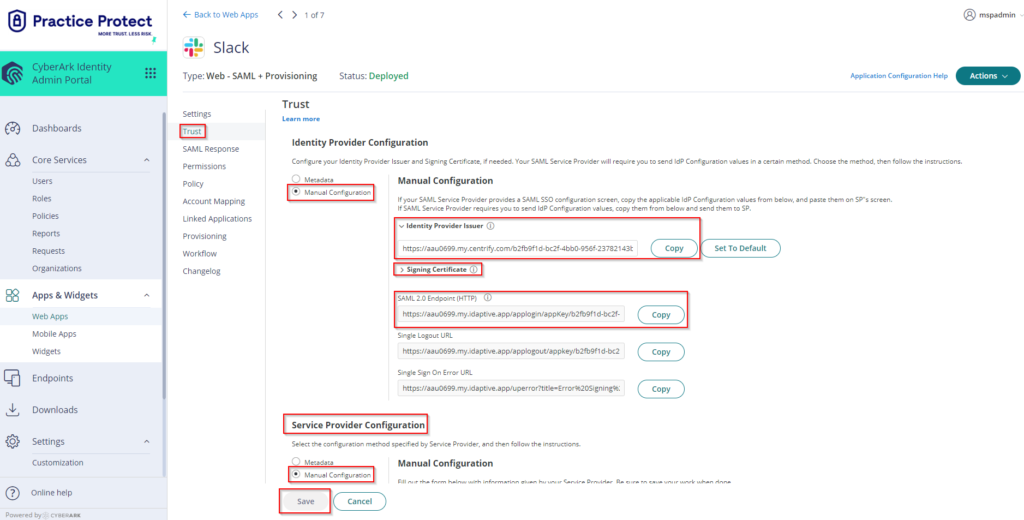
- Click on Permissions > Click Add > Select the Role created on step 2 i.e. “Slack SSO Users”. Click Save.
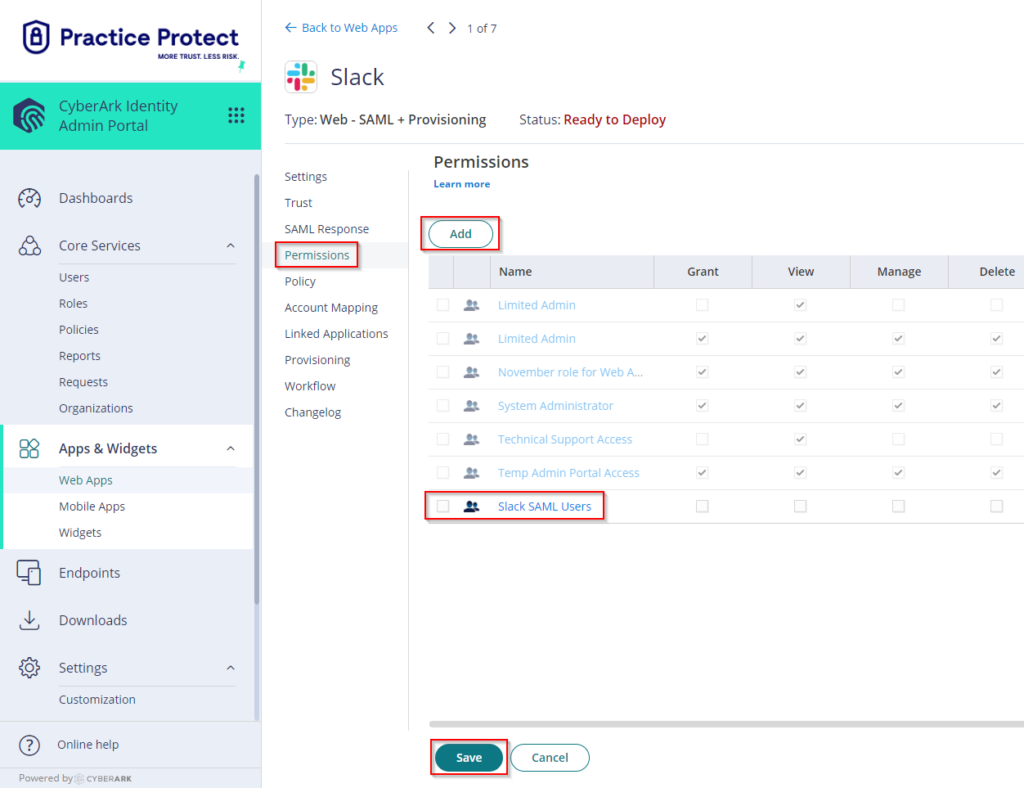
- The status of the application will change from Ready to Deploy into Deployed. This means that the newly added app will now appear on the user portal for all users that are members of the role (i.e. “Slack SSO Users”)
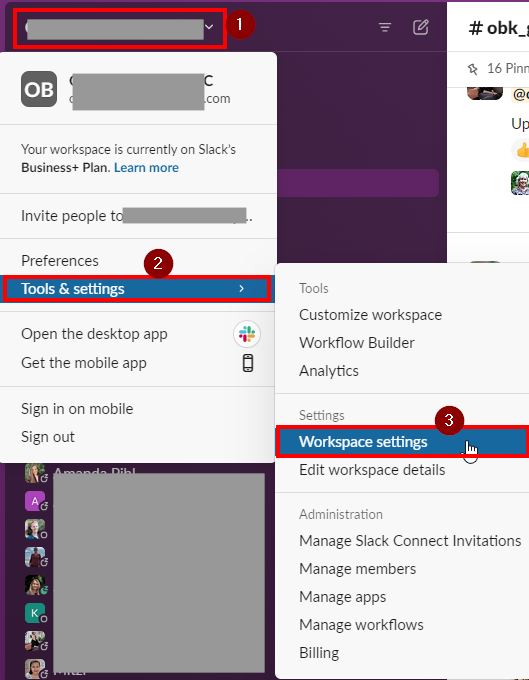
- Login to Slack using the Administrator Account. Click on your company name (i.e. CBP Accountants) > Select Tools & Settings and choose Workspace settings.
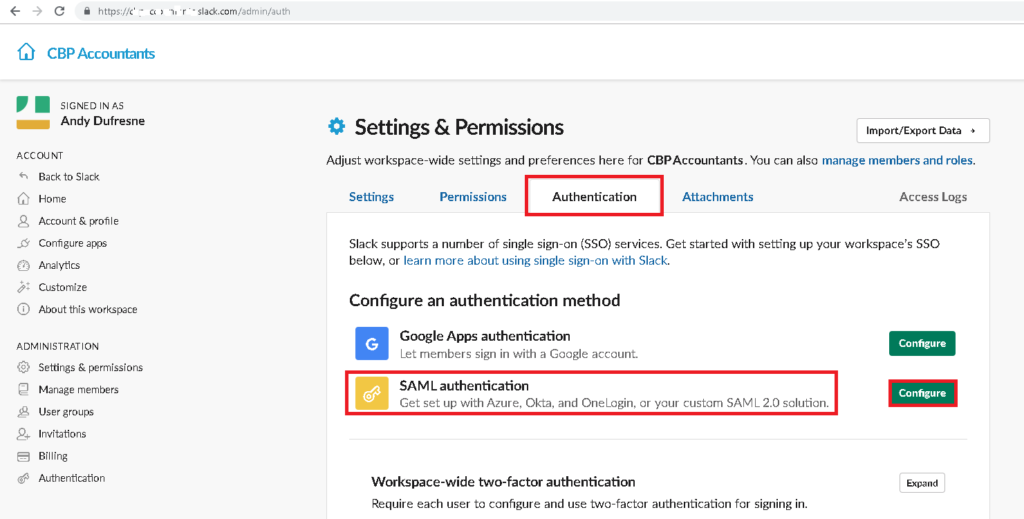
- On Authentication tab. On Configure an authentication method select SAML authentication. Then, click Configure.
-
On Configure SAML Authentication, paste the SAML 2.0 Endpoint (HTTP) and Identity Provider Issuer that you copied from Step 6.
Open the signing certificate file downloaded from Step 6 on a Notepad. Then, on Public Certificate, copy and paste all the characters inside.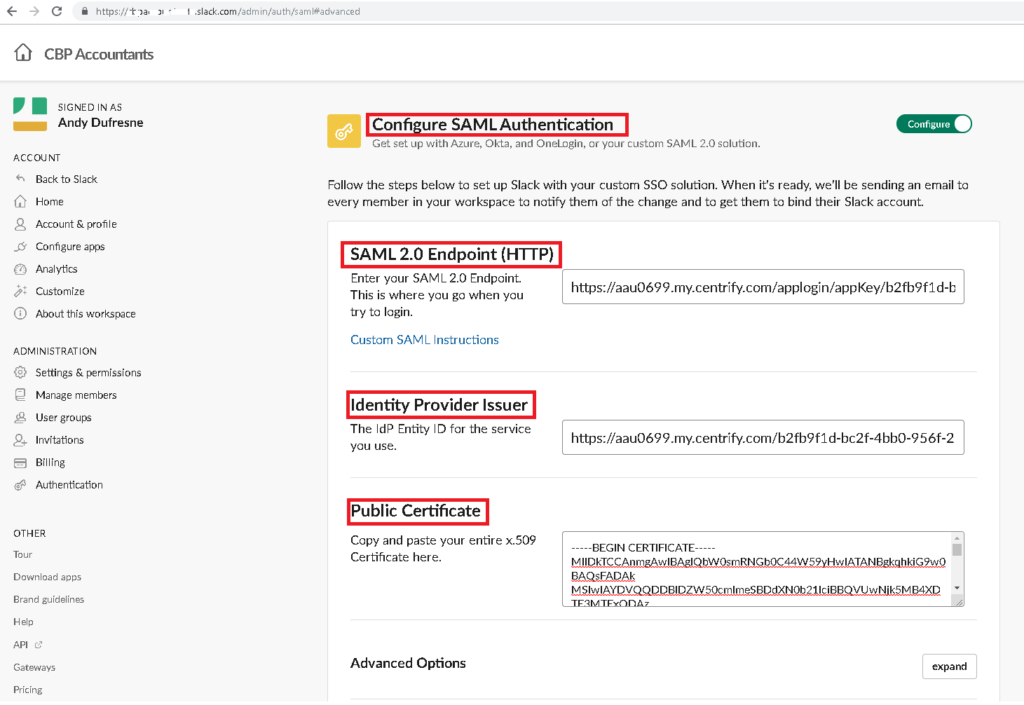
- On Advanced Options click expand. Tick the box for Sign AuthnRequest and copy the public key on the notepad (starts from —–BEGIN CERTIFICATE—– to —–END CERTIFICATE—–) then save it as filename.cer (i.e. SAML_Response_Assertion.cer).
You will use this file later on the Slack app settings in the Portal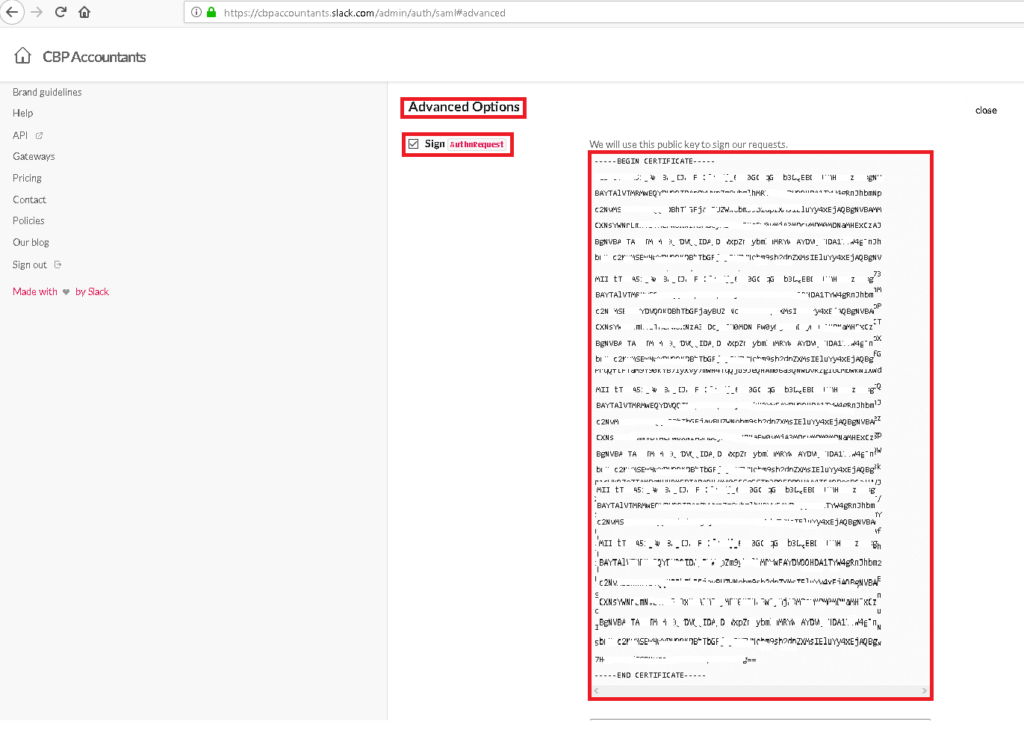
-
Scroll down and untick Assertions Signed. Leave Responses Signed ticked.
-
On Service Provider Issuer, copy the value i.e. https://yourdomain.slack.com on a notepad.
-
On Settings, only tick the box for “Update profile each time a user logs in.“
-
With the Authentication for your workspace must be used, select All workspace members
Important! Once configuration has been saved, selecting this enforces users to login using Practice Protect credentials only.
To test you can just select It’s optional (this means that you will have the option to sign with either through Practice Protect or basic username and password for Slack). -
On Customize, Enter Practice Protect on Sign In Button Label field.
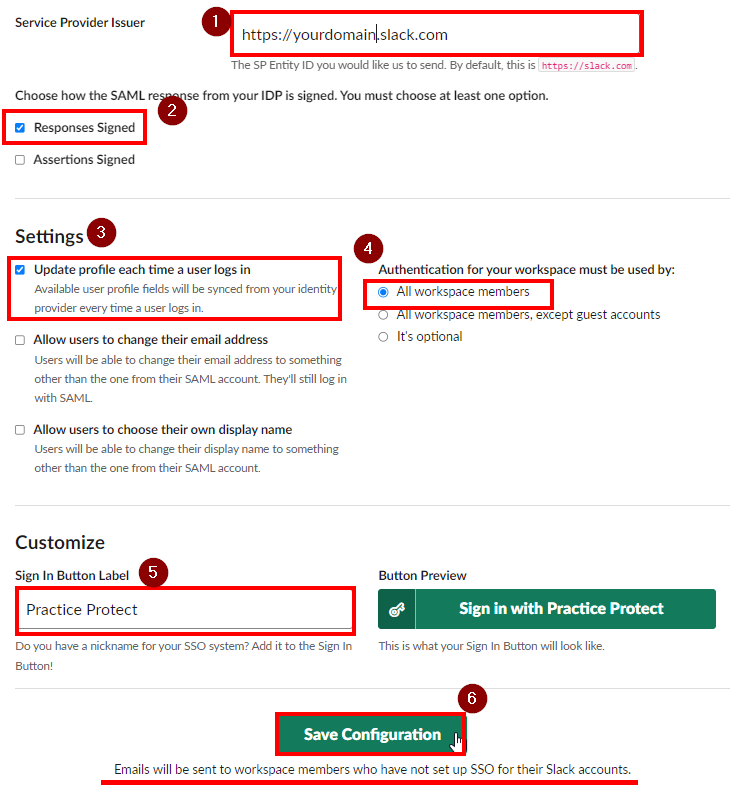
- Click Save Configuration. This applies the configuration setup above.
Important! If you enforced SSO Sign as their sign in method, they will get an email. The email will prompt them to bind their Slack accounts with Practice Protect. Users will have 72 hours to bind their account before the link expires.Any users already signed in when SSO is enabled will remain signed in.
Going forward, all members will sign in to Slack with their IDP account. If you chose to require SSO, your members will see a sign in page before they can access your workspace.
- Return to the Admin Portal in Practice Protect. Go back to the Slack SSO App Settings and go to Trust.
- Scroll down to Service Provider Configuration > Select Manual Configuration. Enter the value of SP Entity ID / SP Issuer / Audience. (It should be the same details you got from step 14 i.e. https://yourdomain.slack.com). For Assertion Consumer Service (ACS) URL just add the line /sso/saml after URL (i.e. https://yourdomain.slack.com/sso/saml)
On Recipient, tick the box beside Same as ACS URL. Tick the box beside Encrypt SAML Response Assertion then click Choose File then upload the certificate that you saved on step 11 (i.e. ). Click Save.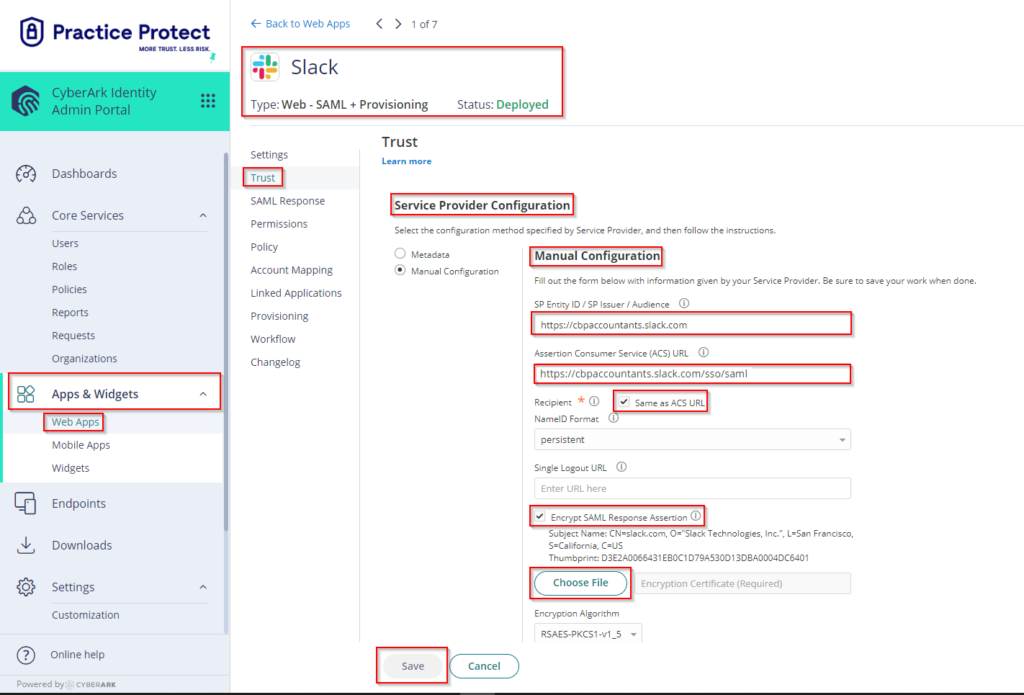
- Single Sign-on is now enabled. Test if it is working by logging into a user account at Slack Login. Select Sign in with Practice Protect.
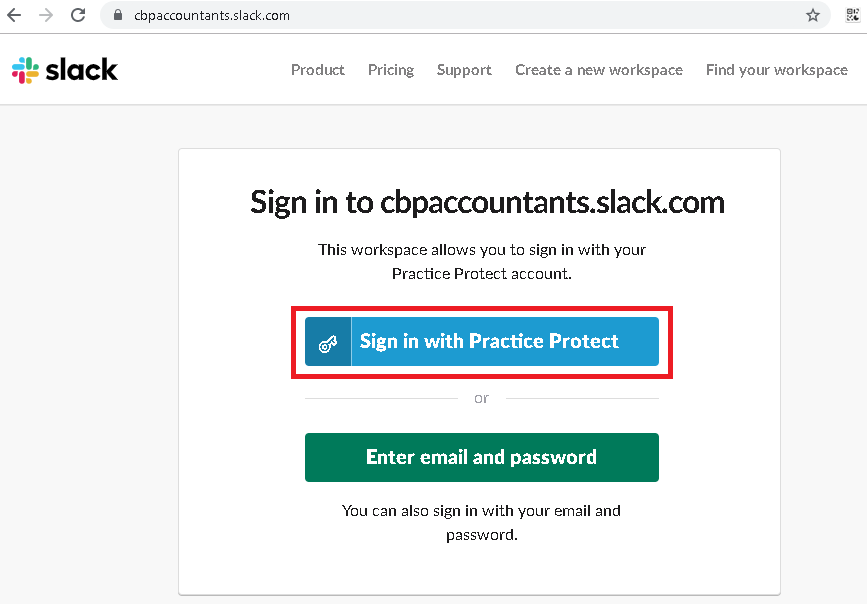
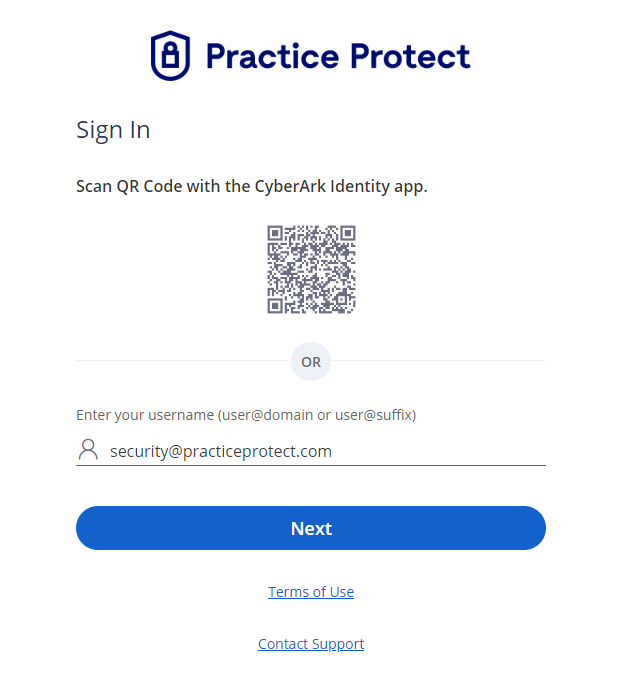
- You will be redirected to the Practice Protect login page. Enter your Practice Protect credentials.
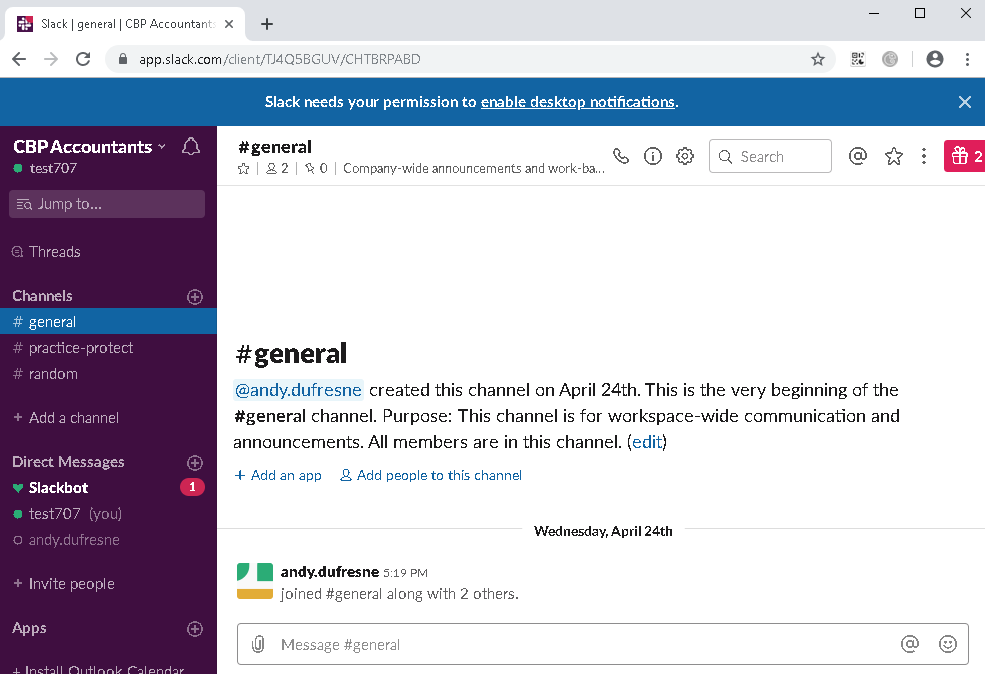
- Once authentication is successful, you should be able to access your Slack application.
Enable Provisioning (Optional)
Enabling provisioning means that you can create users in Practice Protect and will automatically provision users in Slack. Once auto provisioning is enabled you do not need to create the user in Slack manually as it will just sync the users attributes from the platform.
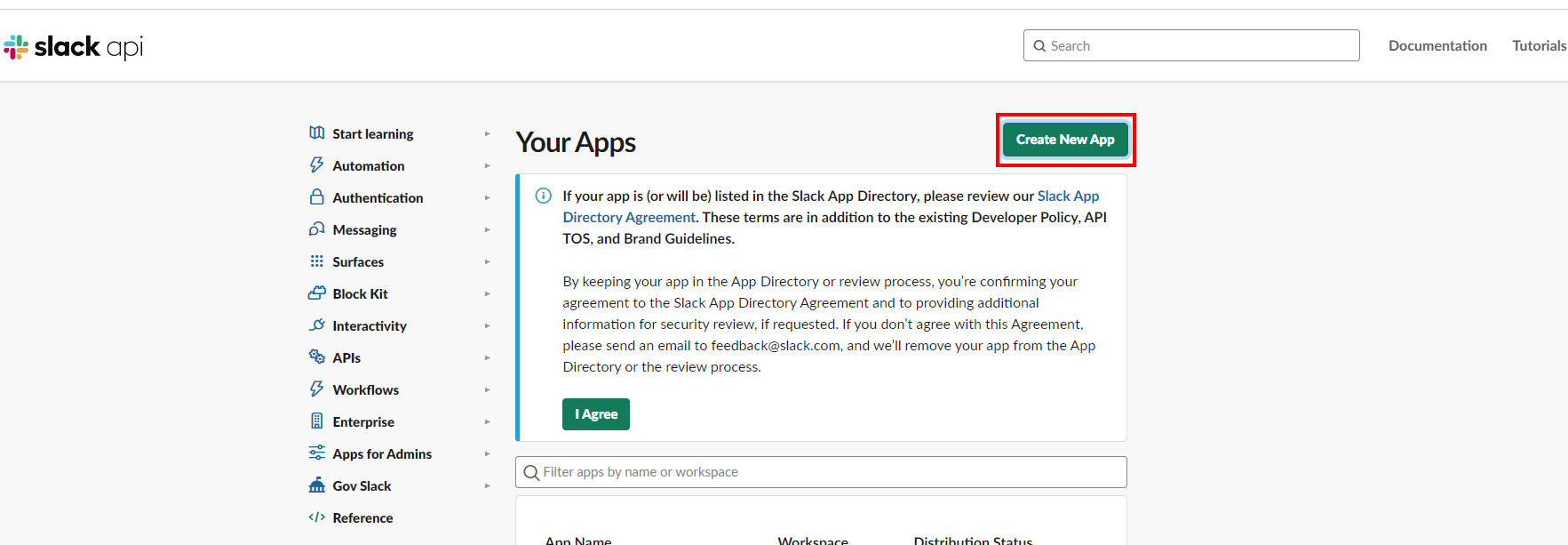
- Go to Slack API and click on Create New App
- On the form, choose “From Scratch“.
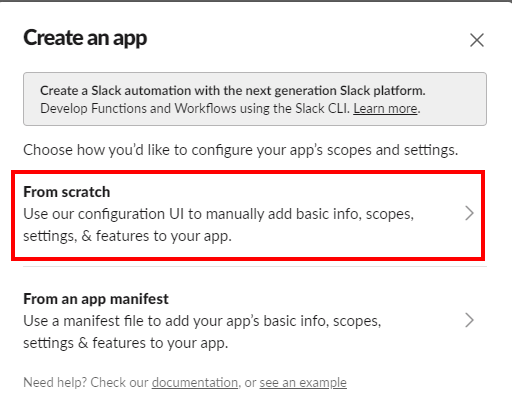
- Enter App Name (e.g. PracticeProtectApp) and select your organization’s workspace.
- Click, Create App.
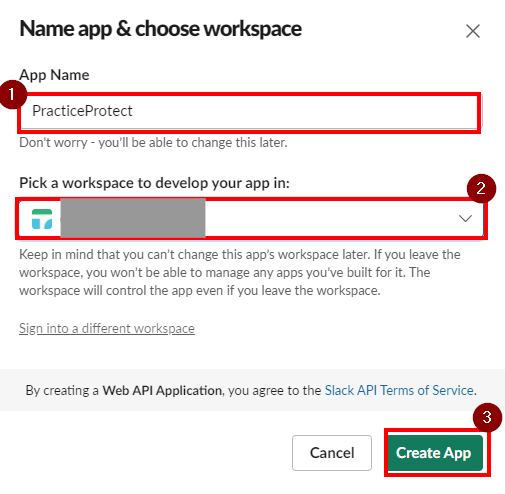
- Go to OAuth & Permissions and click Add New Redirect URL from Redirect URL’s section
- Add this URL: https://pod0.idaptive.app/UserProvOAuth2/AuthzCodecb
- Once added, click Save URL’s
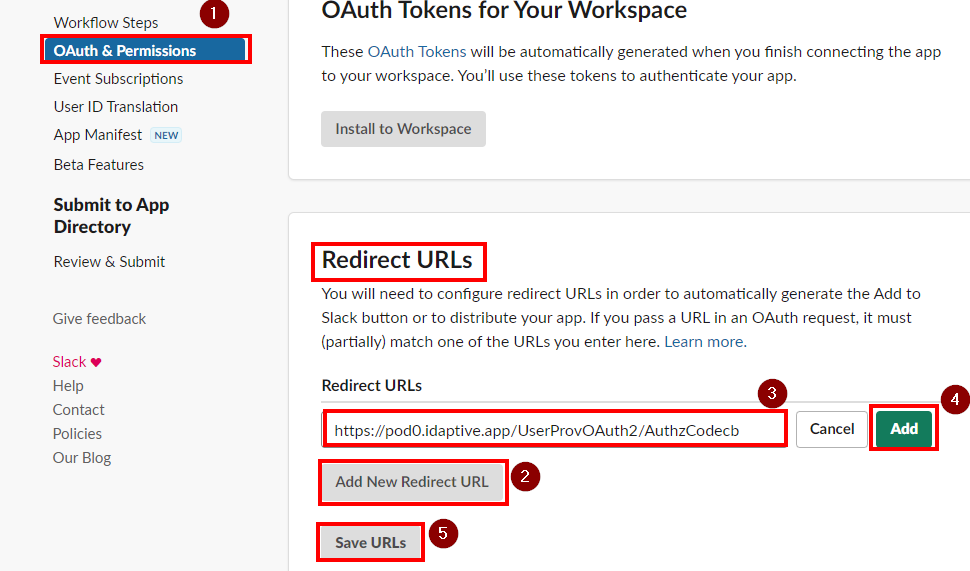
- Return to the Slack SSO App Settings in the Practice Protect Admin Portal.
- Click on Provisioning. Tick the box beside Enable provisioning for this application then click on Authorize.
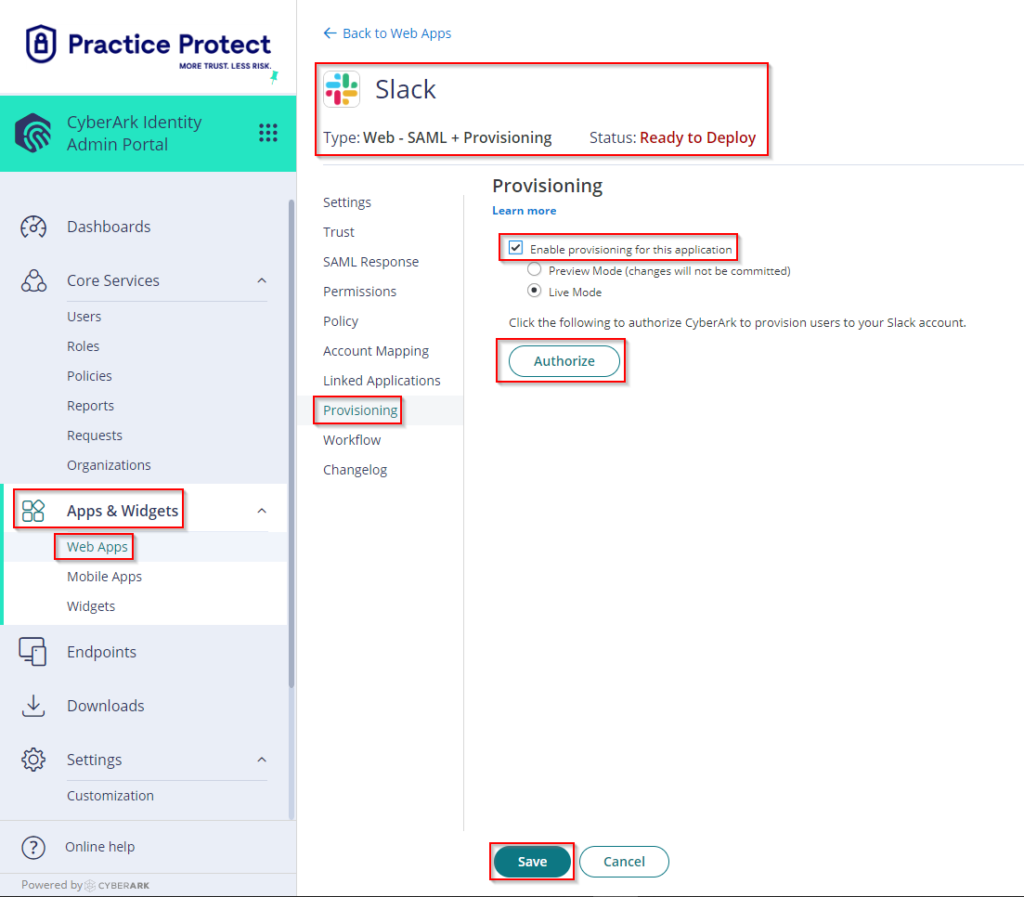
If you encounter an error with “Redirect_uri did not match any configured URIs.“, Please reach out to our support team. - This opens a new window where you need to login using an administrator account to authorize Idaptive to provision users. Enter your Workspace Name and click Continue. Then login as the Administrator in Slack.
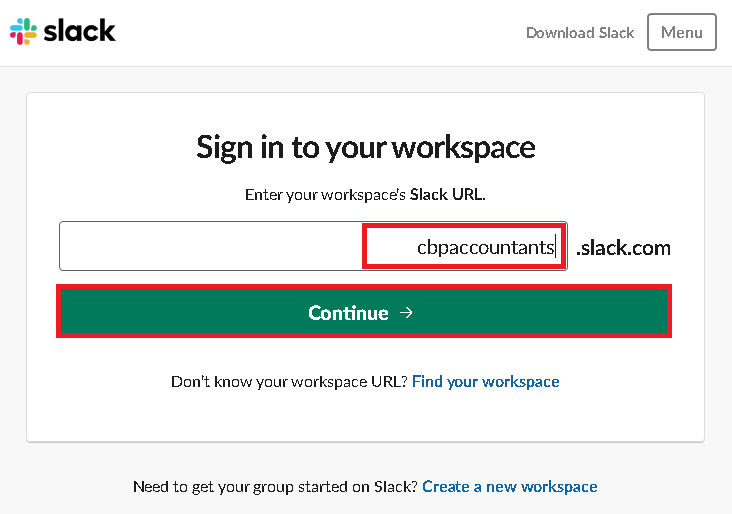
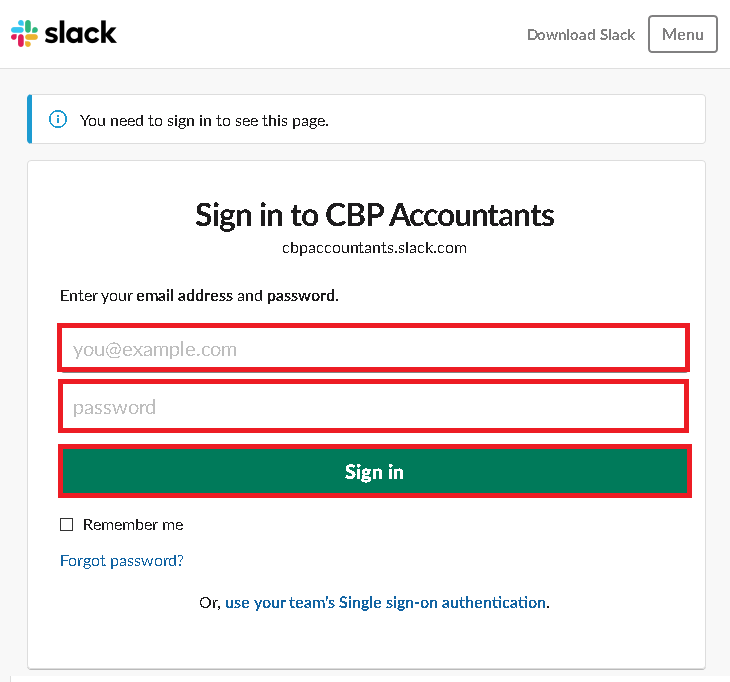
- Click Authorize when prompted.
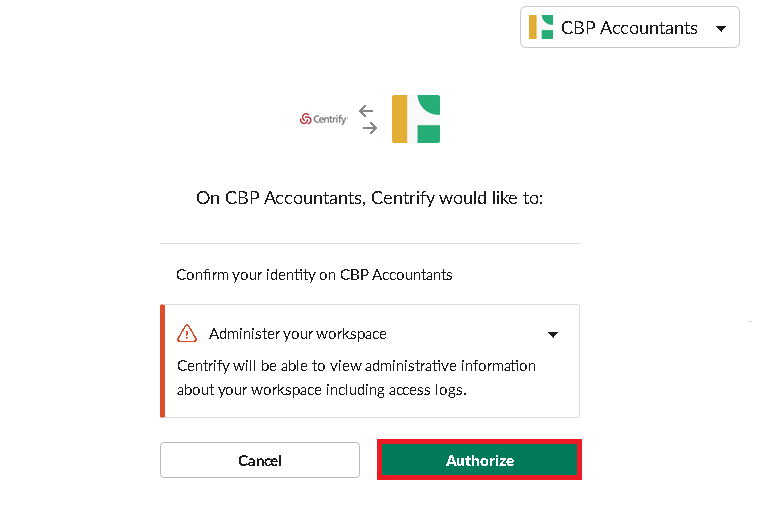
- Wait for a few minutes to complete the Authorization.

- Close the window and Click Save. You may need refresh or reload rights of the current admin portal page.
- Go to Apps > Web Apps > Click on Slack Web – SAML + Provisioning > Click on Provisioning > On Sync Options: Select Sync (overwrite) users to target application when existing users are found with the same principal name. Leave Do not de-provision (deactivate or delete) users in target application when the users are removed from mapped role ticked.
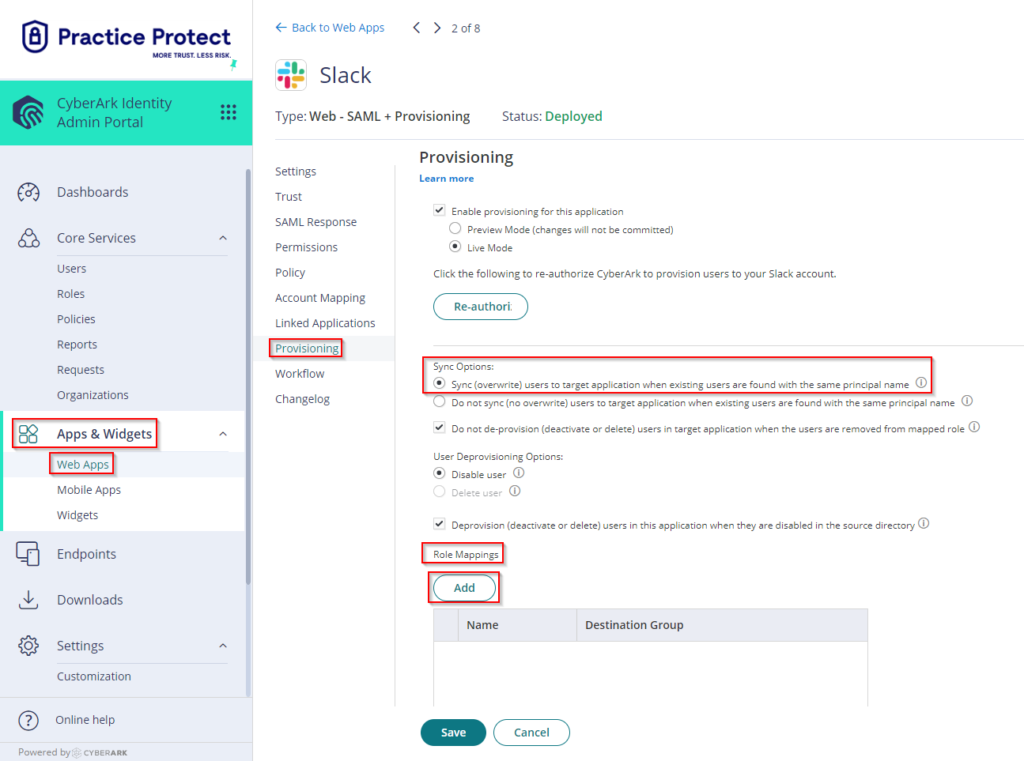
- On Role Mappings, Click Add. Select the respective Role (i.e. Slack SSO users – this is the equivalent group in Practice Protect)
Destination Group (this specifies the equivalent group in Slack if there’s any). On this example, there is no existing destination group in Slack, so we just select Slack SSO Users and this will sync to Slack users group. You may leave this blank or select from the drop down (if you have any existing group in Slack).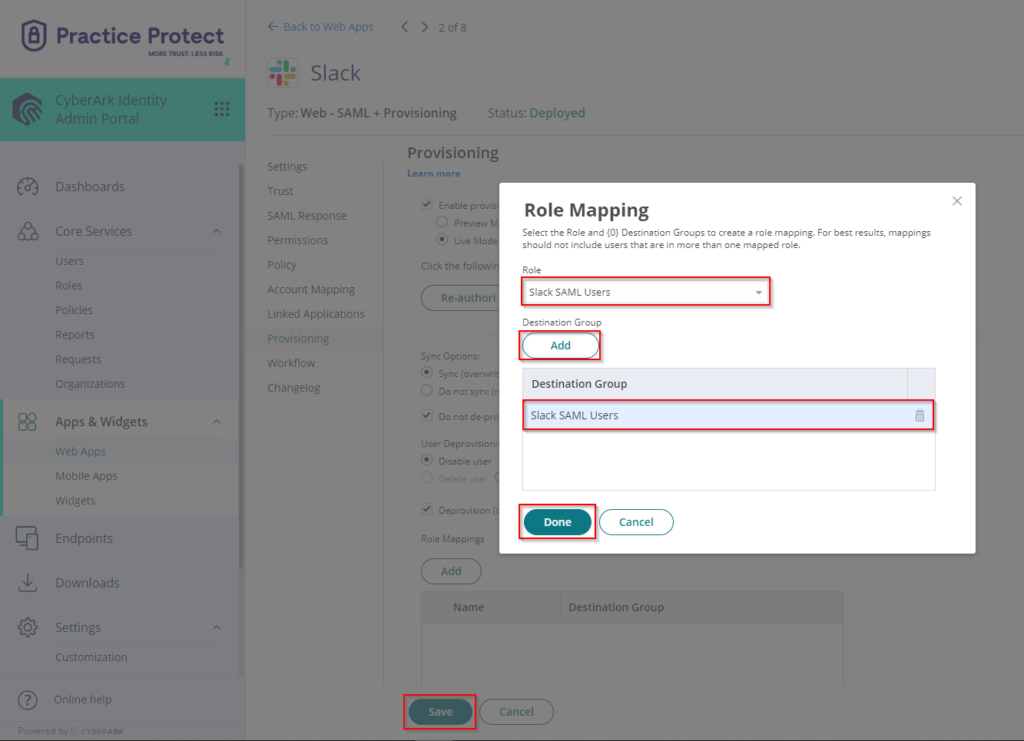
- Click Done and Save.
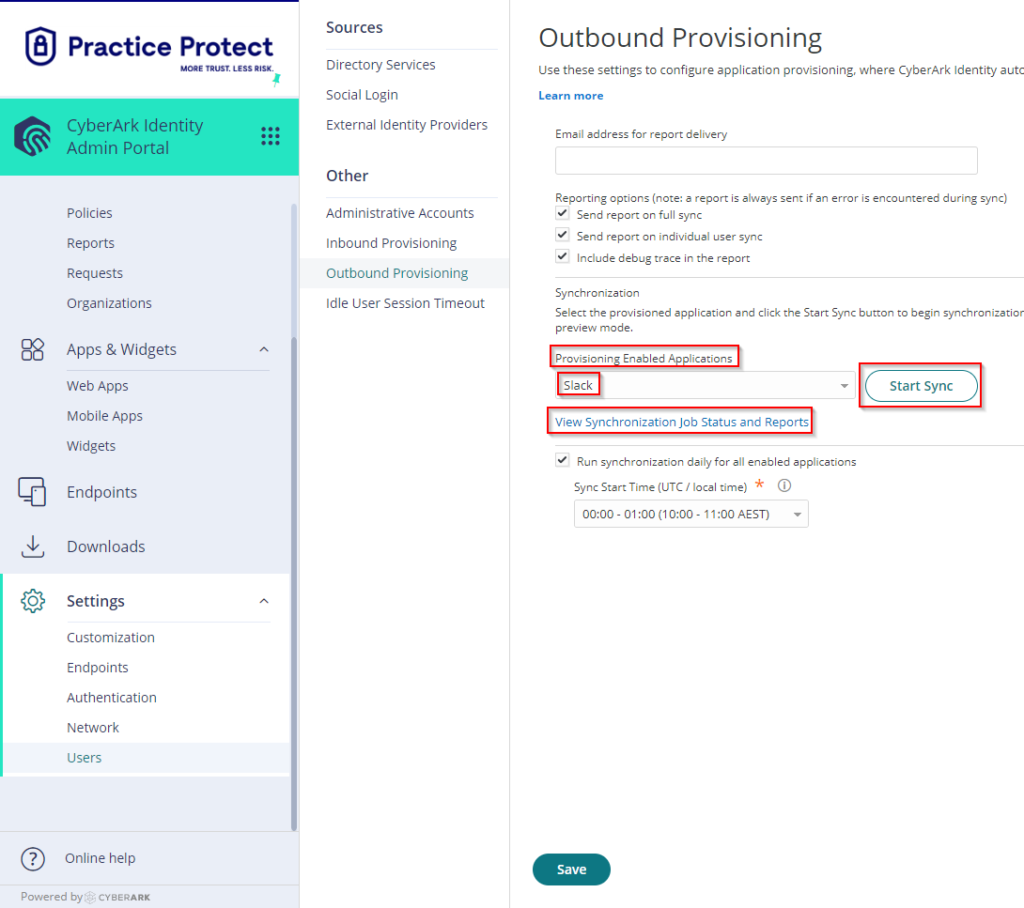
- (Optional) Go to Settings > Click Users > Click on Outbound Provisioning > Tick the box beside Run synchronization daily for all enabled applications > On Sync Start Time (UTC / local time), select the time to run the synchronization. The synchronization runs daily on the specified time.
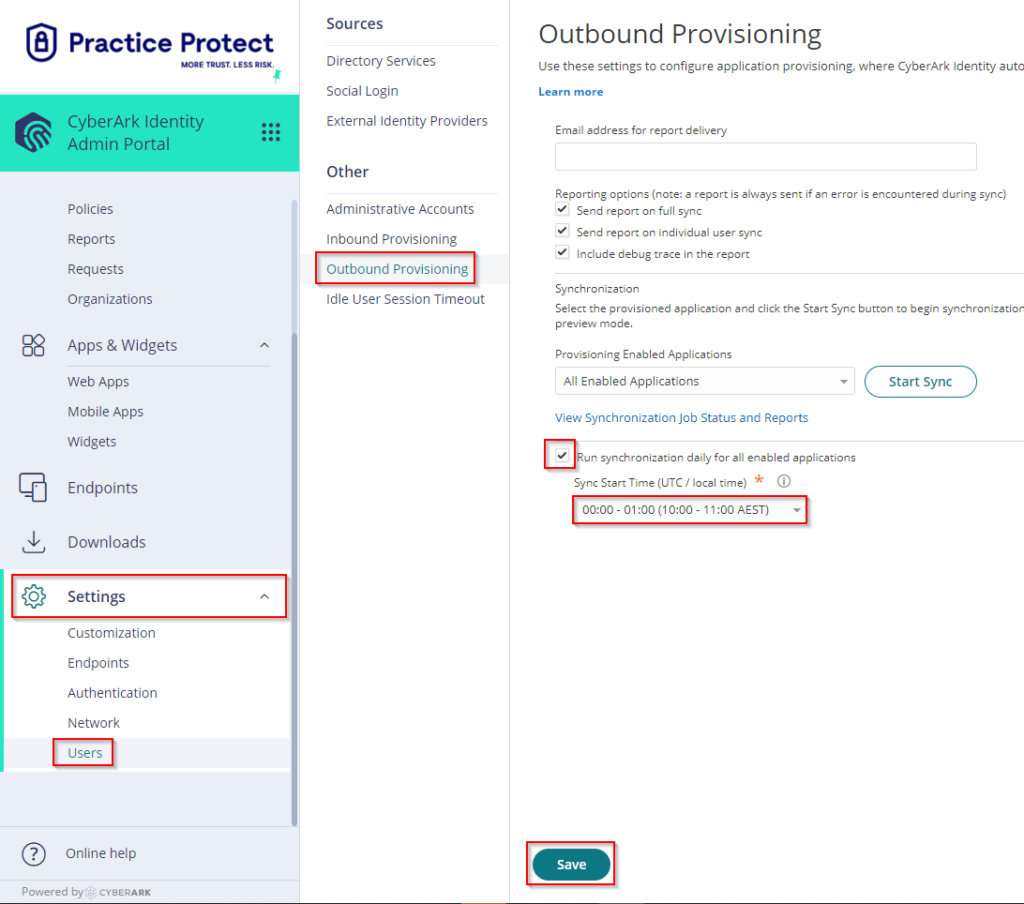
- Click Save. This completes the setup of Slack SSO with provisioning in Practice Protect.
- Run a manual synchronization. Go to Provisioning Enabled Application > Select Slack, then Click on Start Sync.
- You can view the real time status of synchronization by clicking on View Synchronization Job Status and Reports. Once the Synchronization completes any changes in Practice Protect will be reflected in the Slack Admin Console.