Purpose
Weel (Previously DiviPay) offers single sign-on via an OpenID integration with Practice Protect. This provides a seamless login experience to the Weel platform including the mobile application.
When logging into the Weel mobile app, you may briefly see a screen from amazoncognito.com. This is an expected behaviour as part of Weel’s secure login process and is completely safe. It helps verify your login in the background, especially on iOS devices.
Prerequisites
- Requires Weel Enterprise Plan, or purchase of SSO add-on with the Weel Premium Plan
- Admin Access to Practice Protect
- The Username/Email Addresses configured in Weel should match the login names in Practice Protect
Instructions
- Login to your Practice Protect and switch to the Admin portal.
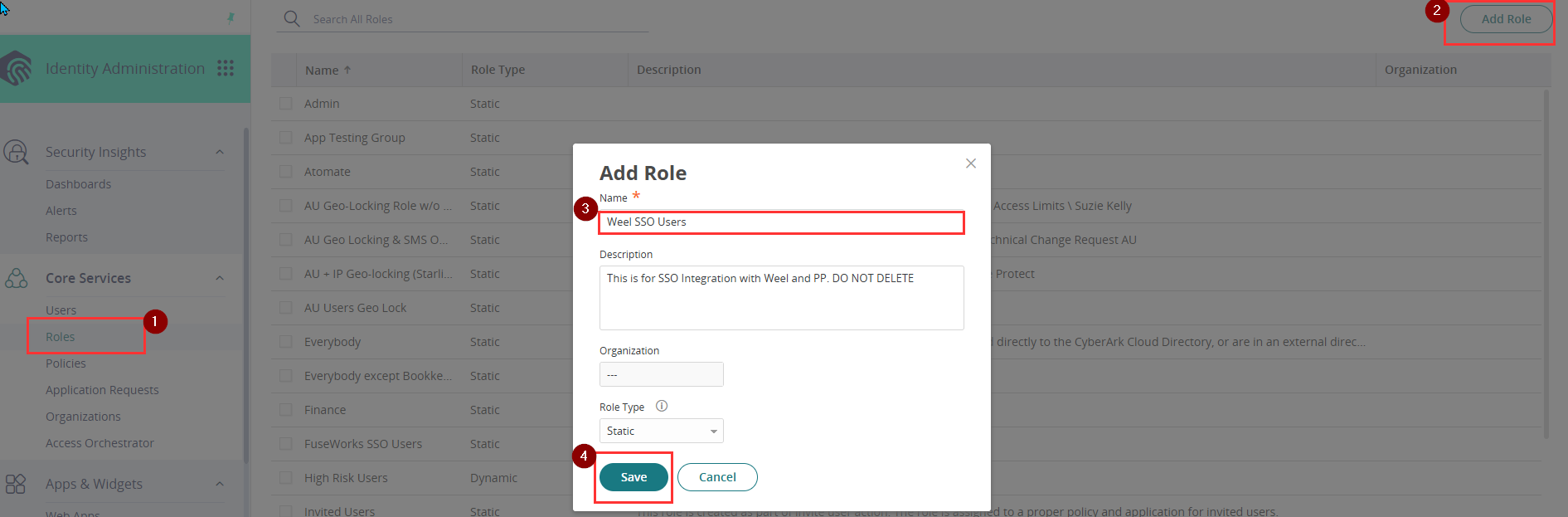
- In Core Services, go to the Roles section and click Add Role. Create a new role by entering Weel SSO Users in the Name field, then click Save.
- With the created role, click on Members > Add. Add each member/user that should be included in the SSO. Then select Save.

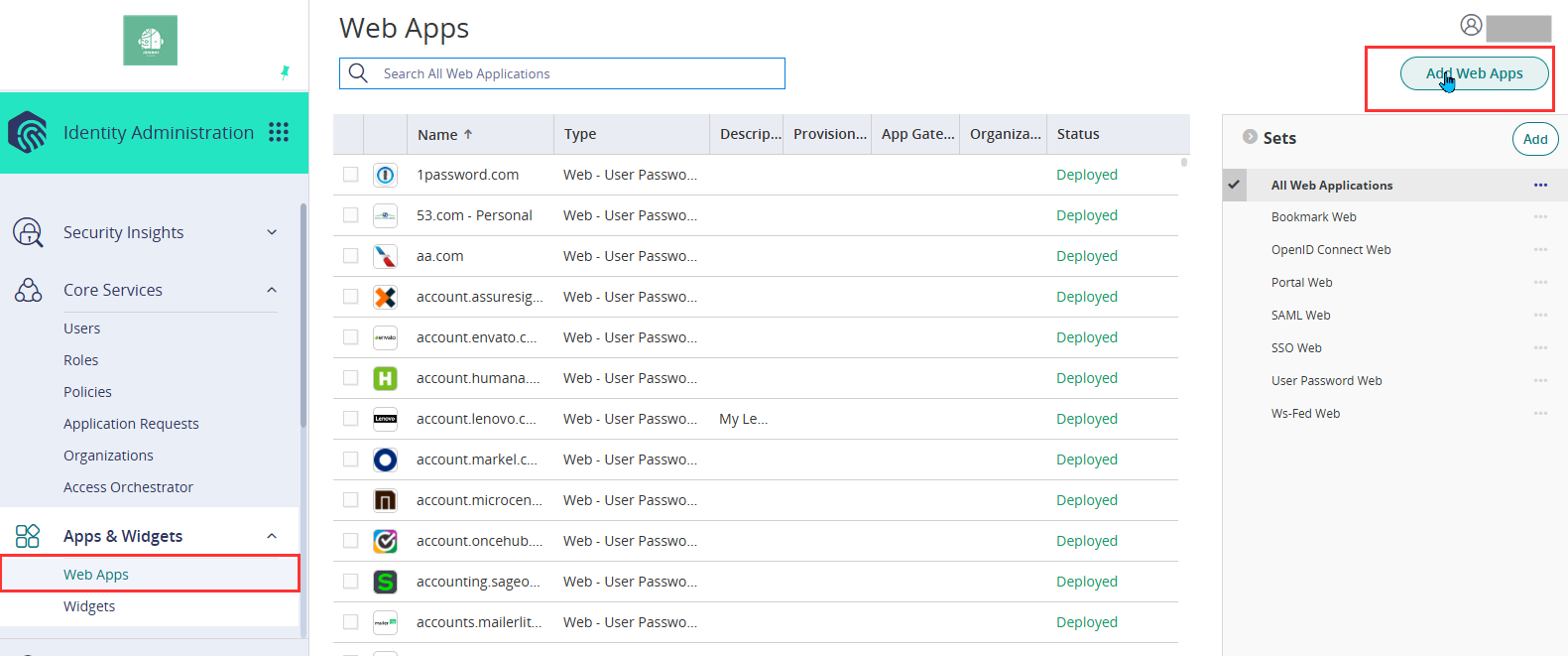
- From the Apps & Widgets, go to Web Apps section and click Add.
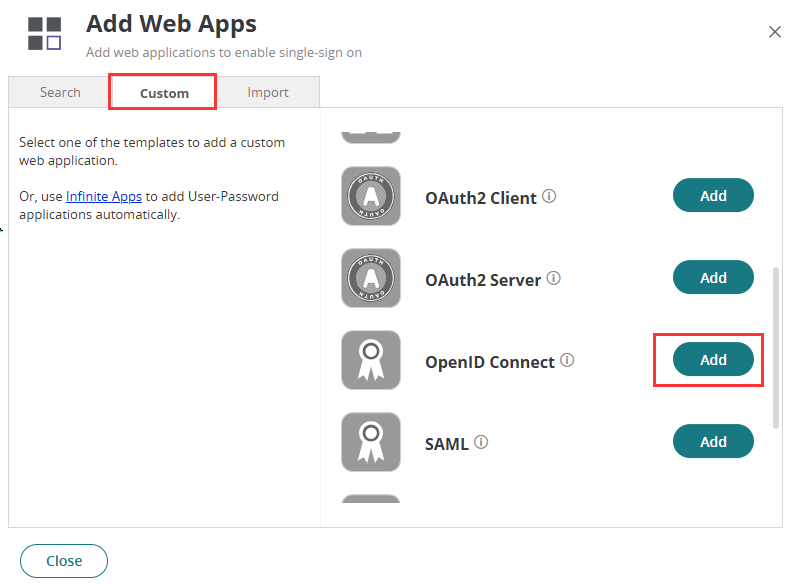
- Then, choose Custom and select OpenID Connect. Click Add.
- Click Yes to add.
- The application that you just added opens to the Settings page. Set the following details:
- Application ID: weel
- Name: Weel OpenID
- Description: This app is configured for Weel and Practice Protect SSO integration.
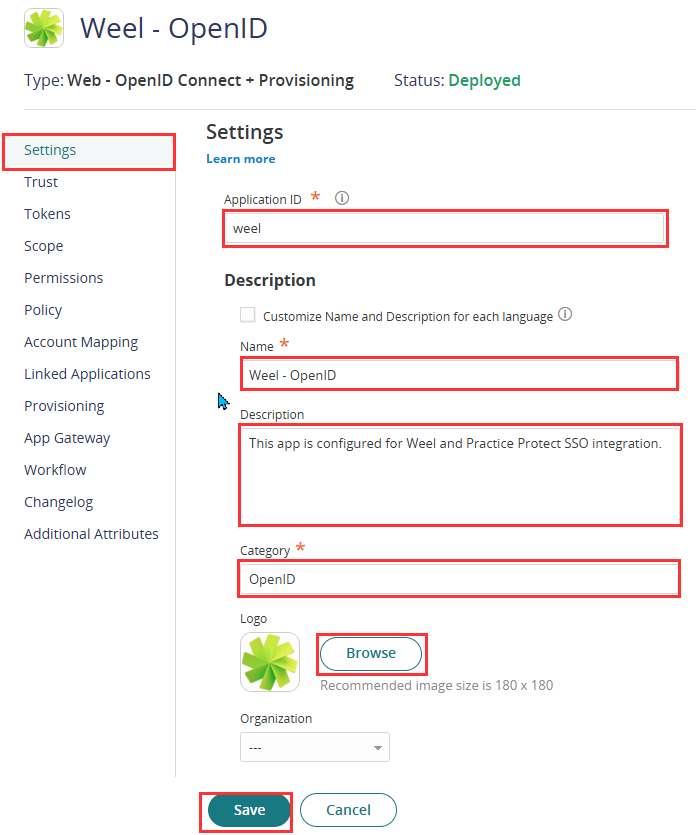
- You can use the logo below as the icon for the app. Just right click and save image as. Note: You can change the name, category or logo based on your preference.

- Click Save.
- Open a new tab and use the password generator tool here. Generate a password for the Client Secret. Important! Select only Numbers, Lowercase and Uppercase, and set the Length to 16. Then, click Generate.
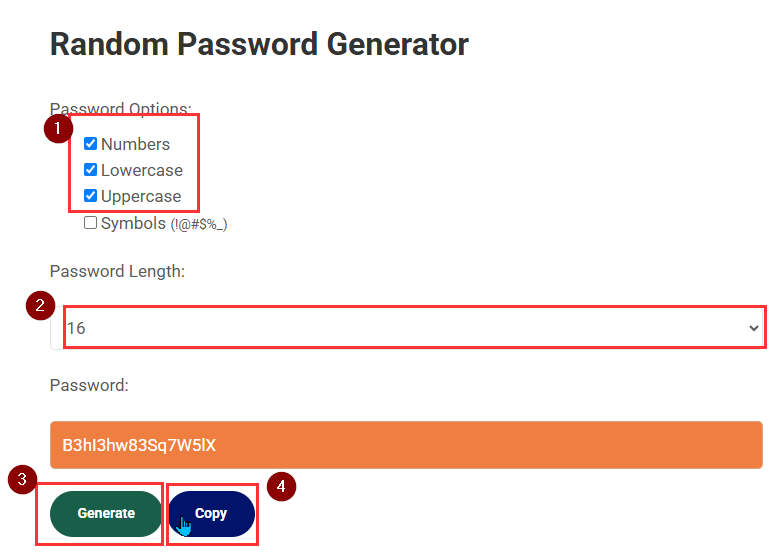
- Copy the password and keep it, as it will be used in later steps.
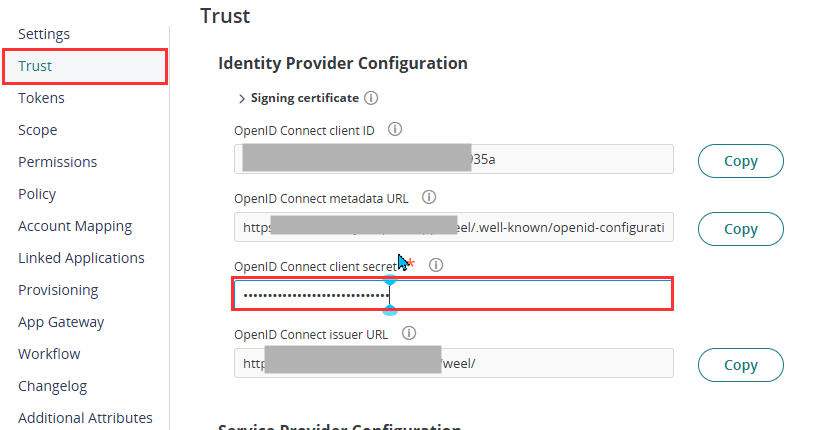
- Return to the Weel SSO app in Practice Protect. On the Trust section, paste the password into the Open ID Connect Client Secret field.
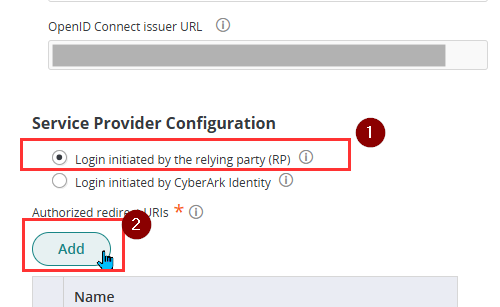
- On the same page, go down to Service Provider Configuration and choose Login initiated by the relying party (RP)
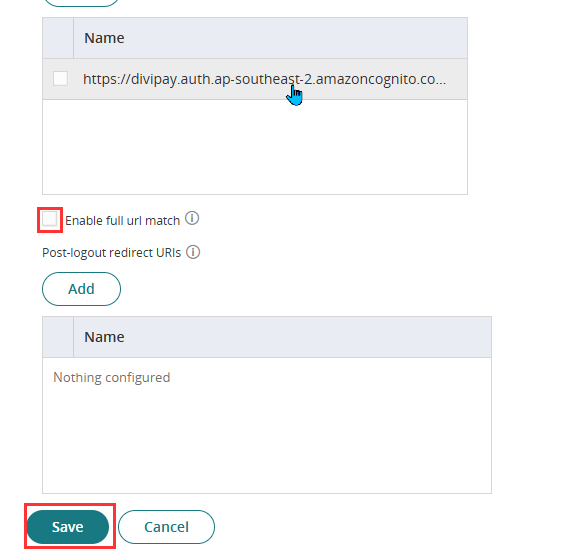
- Under Authorized Redirect URIs, click Add.
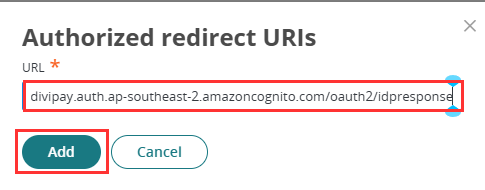
- Add this URL:
https://divipay.auth.ap-southeast-2.amazoncognito.com/oauth2/idpresponse
- Untick the box for Enable full url match
- Click Save.
- Go to Permissions page and click Add.
- Find the role created in Step 2 (e.g. Weel SSO Users), select it and Add.
- Click Save.

- Return to the Trust page and take note of the Client ID and Issuer URL, as these will be used in the next step.
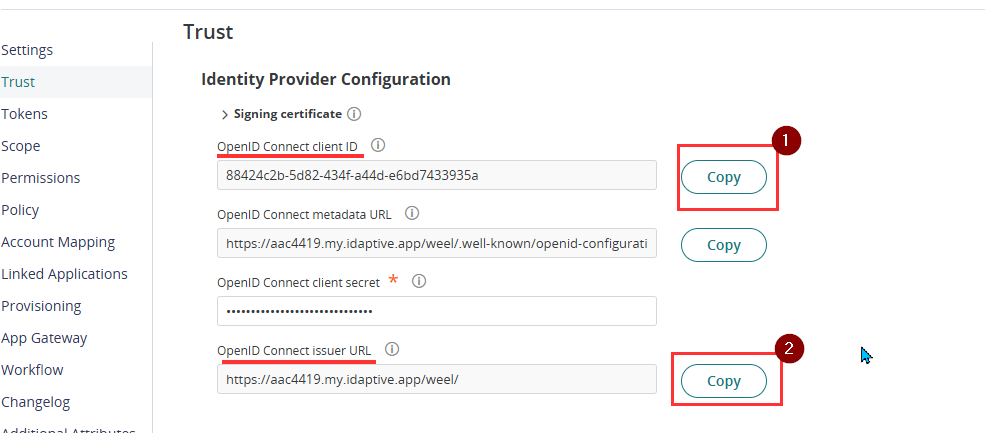
- Submit the SSO configuration details to Weel by completing the form at the following link. Below is the sample question/answer in the form
- Select your SSO provider type: OIDC
- Enter OIDC Issuer URL: Paste the Issuer URL copied from Step 19
- Enter OIDC Issuer ID: Paste the Client ID copied from Step 19
- Enter OIDC client secret: Paste the client secret generated from Step 9
- Enter OIDC scopes: N/A
-
- Once submitted, Weel Support will complete the configuration and they will coordinate with the admin or a test user to verify the SSO connection.
- Download the Weel SSO Autofill app. This is the app we will deploy for all users
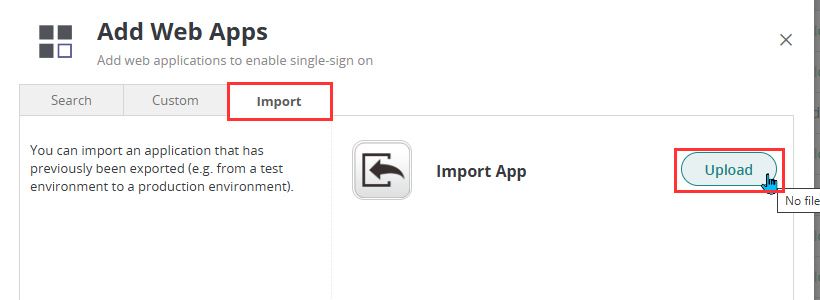
- Return to Practice Protect Admin Portal and go to Apps & Widgets > Web Apps > Click on Add Web Apps in the top-right corner.

- Select the Import tab, then click Upload. Choose the Weel SSO Autofill file you previously downloaded.
- After the file has been successfully uploaded, close the form window. The settings page for the app will open automatically. If it doesn’t, simply locate the app in the Web Apps and open it.
- Navigate to the Description section and rename the app by updating the Application Name field (e.g., change it to Weel SSO).
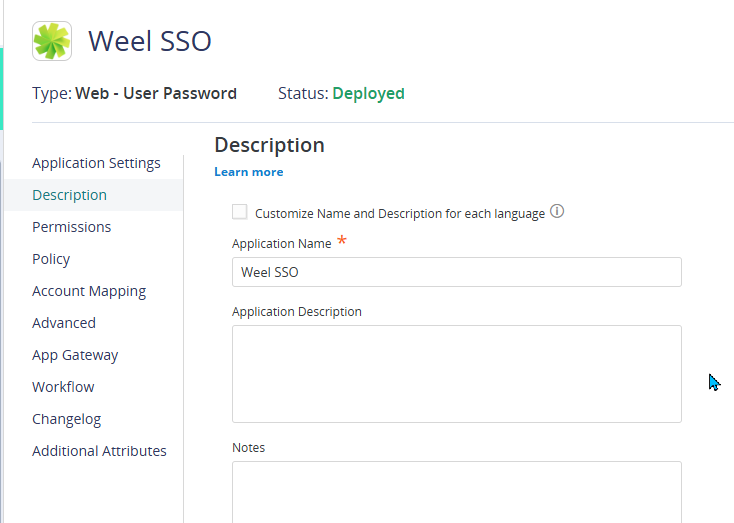
-
Go to the Permissions tab and add the Weel SSO Users role that you previously created.

- The Weel SSO app is what each user will see and use to launch and log in to Weel. The Weel OpenID app, on the other hand, is where the Single Sign-On (SSO) integration is configured.
-
After successful testing and confirmation that it is working, please revert to Weel Support so they can activate it for all users, if they haven’t already.
Please note that onboarding new users to Weel remains the same, you still need to create the user in Weel manually. Make sure the user has an account in Practice Protect with the same username, and ensure the user is also assigned to the Weel SSO Users role.
