Purpose
Before disabling legacy authentication in your Microsoft 365 environment, ensure that your users’ applications support modern authentication. Legacy authentication, used by older protocols like POP3 or IMAP, lacks advanced security features. Review the Sign-in logs in the Microsoft Entra ID admin center to identify any apps or users relying on legacy authentication and assess potential impacts on functionality.
View Legacy Protocol and Authentication Logs
-
-
Sign in to the Microsoft Entra ID admin center using an administrator account (typically the same as for Microsoft 365).
-
In the search bar, type Microsoft Entra ID and select it, or navigate to it from the left-hand menu.
-
Under Identity > Monitoring & health, select Sign–in logs.
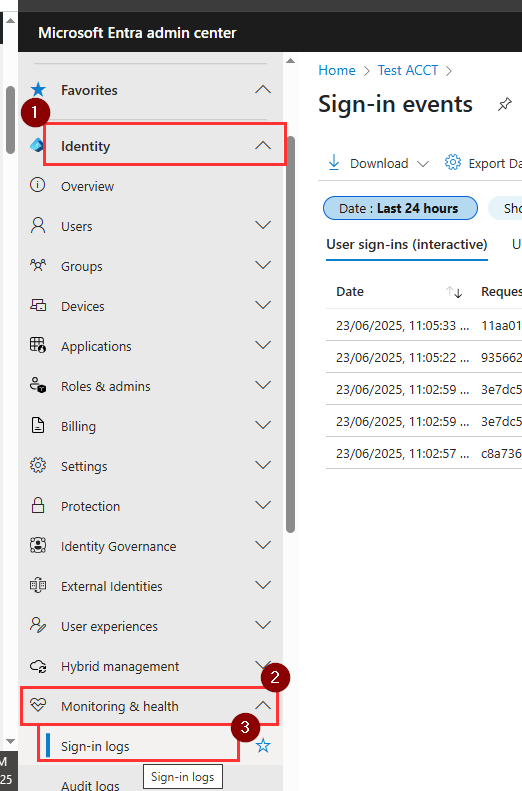
- In the Sign-in logs, filter by Date range (e.g Last 7 days).
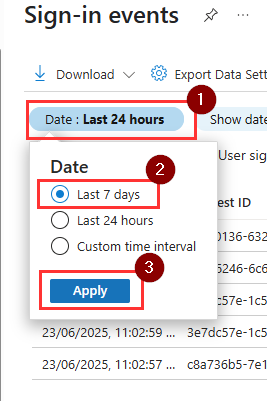
- Click Add Filters, and choose Client App and click Apply.
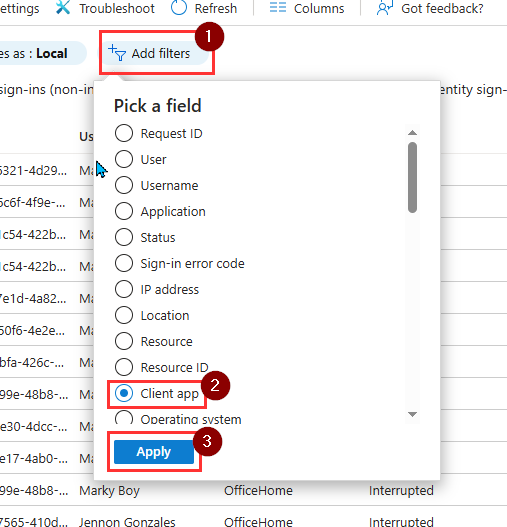
- With client app selected, click on it again and choose, IMAP, POP and SMTP
-
Review the logs to identify any legacy protocol usage (e.g., SMTP for scan-to-email on multifunction printers). Select a log entry for details, including the account and protocol used.
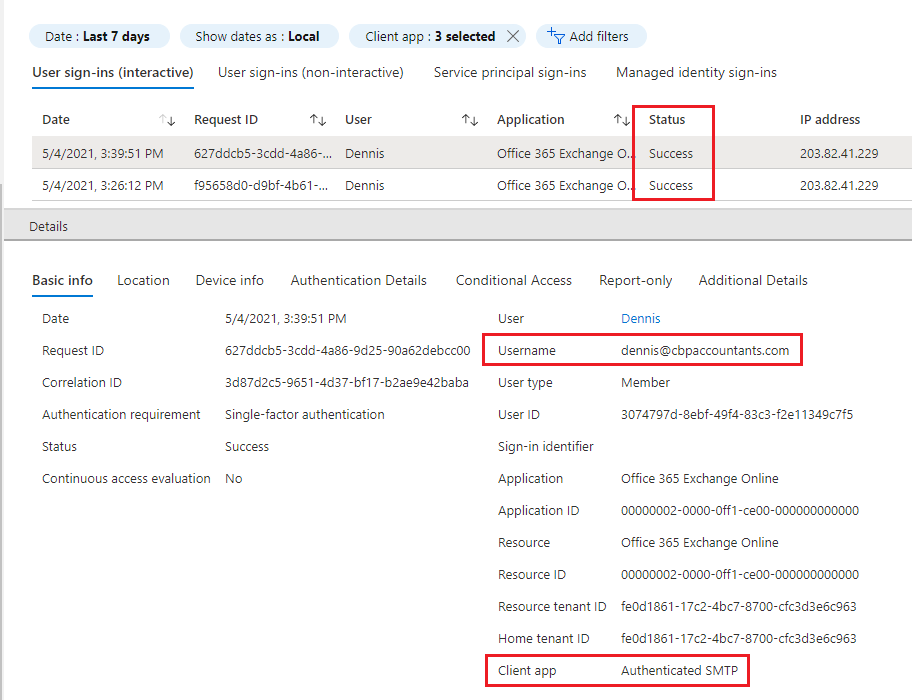
Note: A common use of SMTP is scan-to-email on multifunction printers. To transition printers to modern authentication, configure them to use OAuth 2.0 with Microsoft Graph API or a supported email app. See Microsoft’s documentation: Configure SMTP for modern authentication (Option 3).
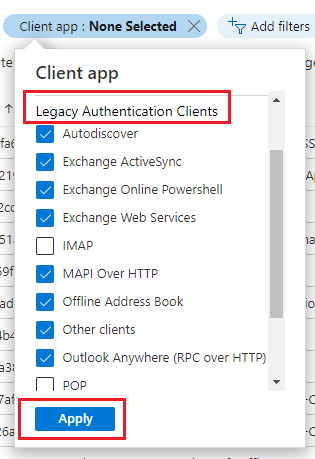
- Filter the sign-in logs by clicking Client App, selecting all options under Legacy Authentication Clients except SMTP, POP, and IMAP, then click Apply to view non-protocol legacy authentication usage.
-
eview the sign-in logs to identify devices or applications still using legacy authentication, such as older versions of Outlook or mobile email apps that do not support modern authentication or MFA. Common examples include ActiveSync and MAPI over HTTP. Once a policy is enabled in Office 365 to block basic authentication, these devices will prompt users to sign in again, and in some cases—especially on mobile devices—users may need to remove and re-add their email accounts.
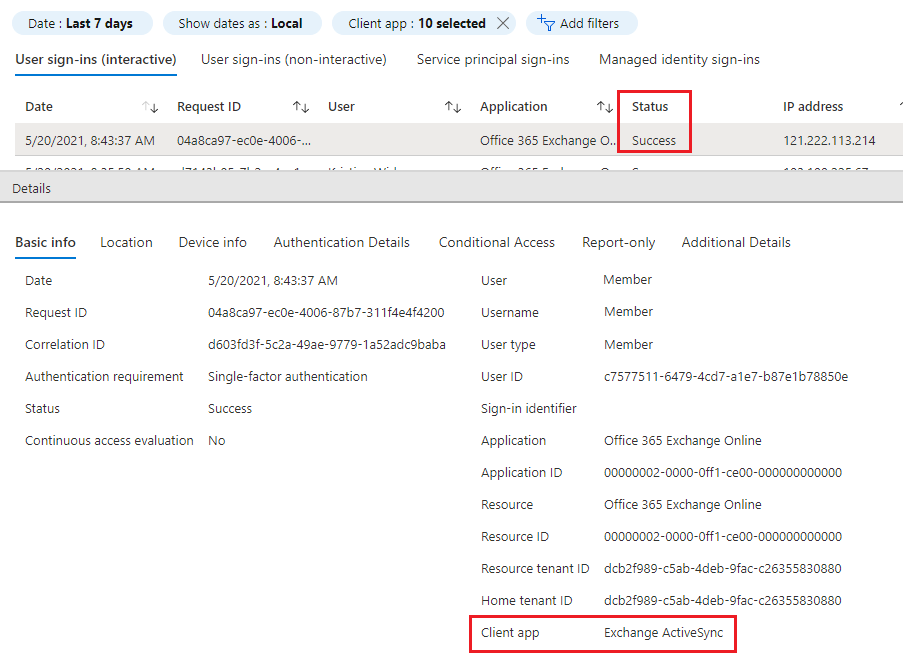
- After confirming that all systems have transitioned away from legacy protocols, proceed to fully secure your Office 365 environment by disabling all legacy authentication and protocols using the steps outlined in the following guide.
-
