Before you can block legacy authentication in your Office, you need to first understand if your users have apps that use legacy authentication and how it affects you. Azure AD sign-in logs can be used to understand if you’re using legacy authentication.
View Legacy Protocol and Authentication Logs
- Login to Azure AD Portal with an Administrator Account. https://portal.azure.com (Note this is the same Administrator Account as Office 365)
- In the Search bar search for Azure Active Directory and Click.
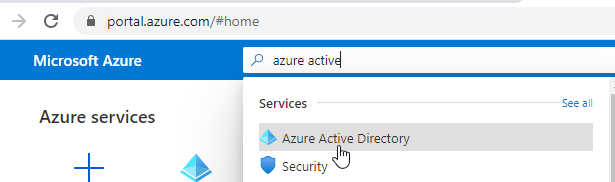
- Scroll down and click on Sign-ins.
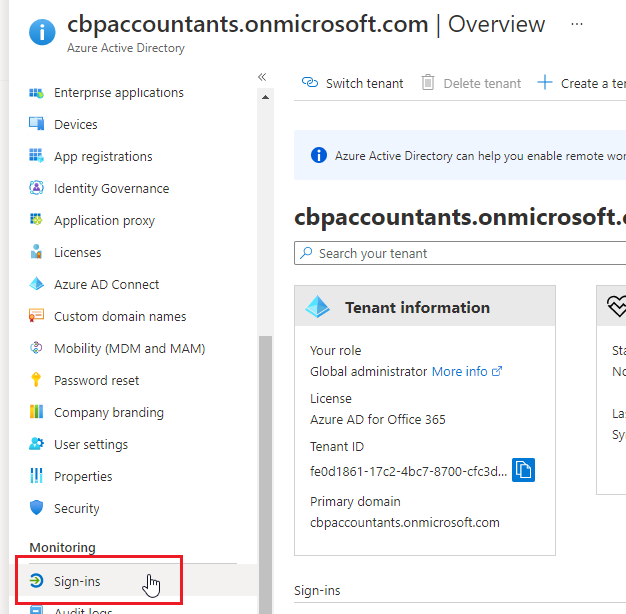
- Click on Date select 7 Days and click Apply.
- Click Add filters chose Client App and click Apply.
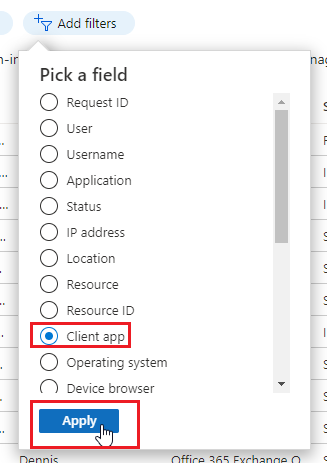
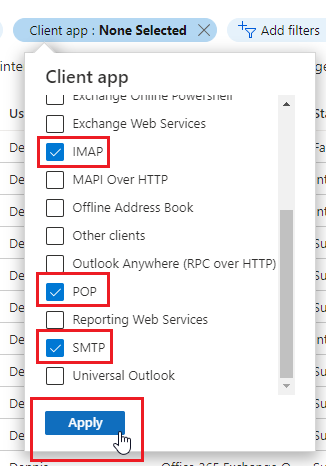
- Click on Client app select IMAP, POP & SMTP and click Apply.
- This will now display the last 7 days of logs where Legacy Protocols (SMTP, POP, IMAP) were used (If Any). For any results click on the log entry for more details. The log entry will show which account and what protocol was used.
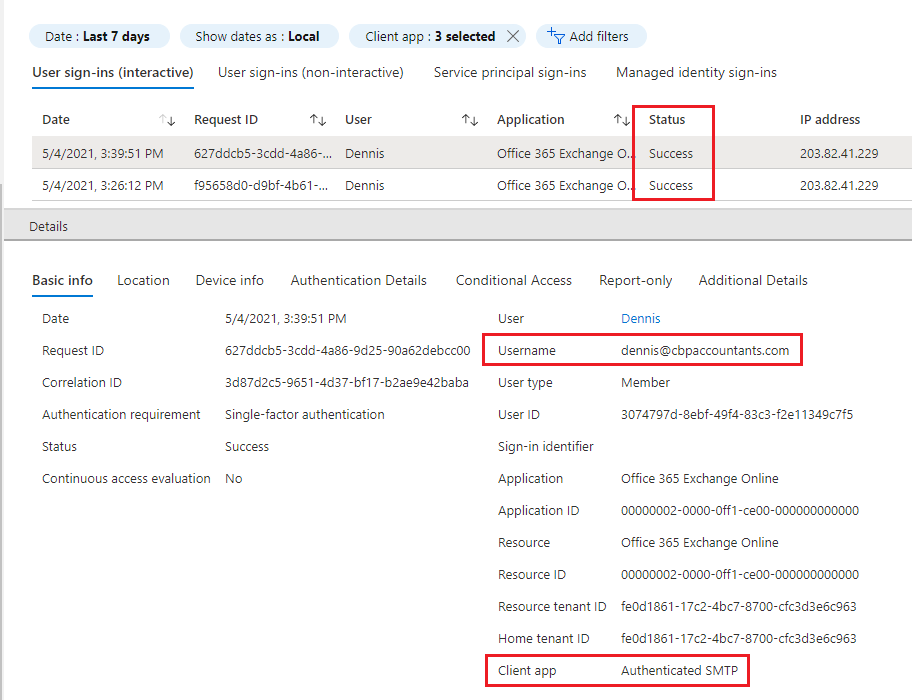
- Most common use of Legacy protocols is Scan to Email from the Office Scanner on SMTP. To transition the printer away from Legacy Authentication follow the steps in Option 3 of the following Microsoft guide.
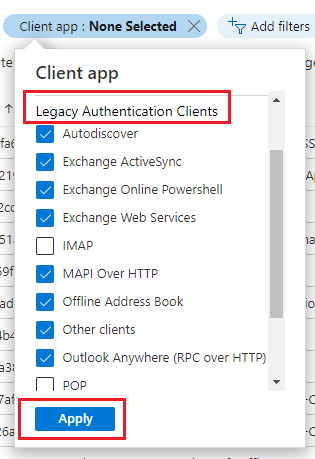
- Now filter the log for Legacy Authentication Use. Click on Client App and select everything listed used “Legacy Authentication Clients” and exclude “SMTP, POP, IMAP” and click Apply.
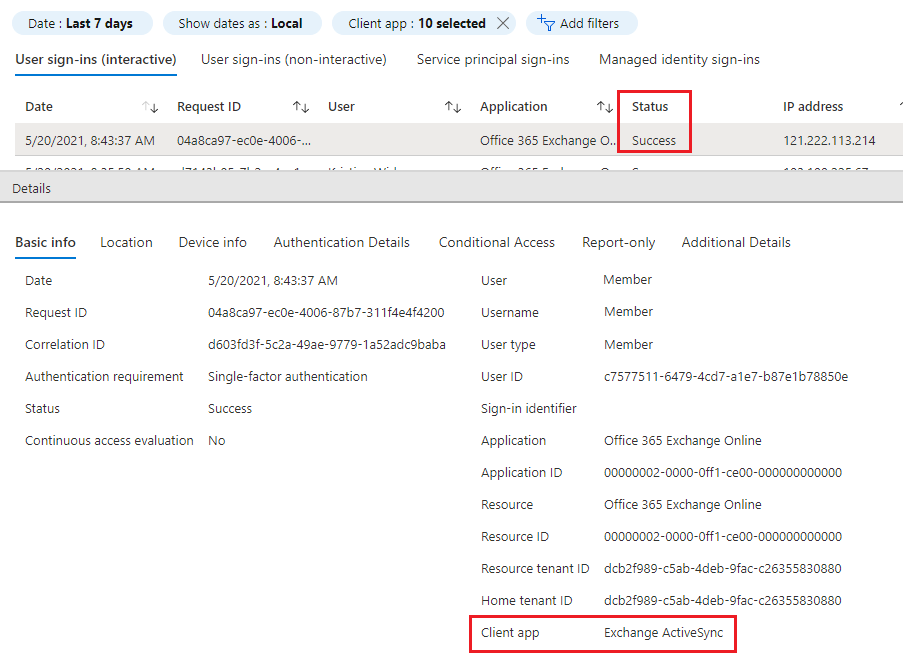
- This will now display the last 7 days of logs where Legacy Authentication was used. The most common are ActiveSync and MAPI over HTTP. This indicates that users have Outlook or Phones connected without Modern Authentication (No MFA). Once you enable policy in Office 365 to block Basic Authentication these devices will prompt for login and users will require to use Modern Authentication. On phones this can require the user to remove the account and re-add it.
- Once all systems are moved off Legacy Protocol use you now need to secure your Office 365 by disabling all Legacy Authentication & Protocols with the following guide.
