Purpose
Attackers targeting accounts using legacy IMAP/POP/SMTP protocols in order to brute-force the accounts using common variations on usernames and passwords exposed in large credentialed dumps.
For MFA and Practice Protect polices to be effective, legacy authentication needs to be blocked at the Microsoft 365 level. This is because legacy authentication protocols like POP, SMTP, IMAP, and MAPI can’t enforce MFA, making them preferred entry points for adversaries attacking your organization.
The numbers on legacy authentication from an analysis of Microsoft 365 traffic are stark:
- More than 99 percent of password spray attacks use legacy authentication protocols
- More than 97 percent of credential stuffing attacks use legacy authentication
- Microsoft 365 accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled
Modern Outlook connections to Microsoft 365 no longer use these protocols. However they are left on my default in Microsoft 365.
Disabling theses protocols and blocking Basic Authentication on your organization’s cloud user accounts is a good measure as well as our recommendation to Federate your Microsoft 365 with Practice Protect. You must take into account any 3rd party applications/devices using SMTP/IMAP to send or access your accounts, as these system may still be using Legacy Protocols and need to be migrated.
Prerequisites
- Office 2016 installed on client computer
- Admin Account in Microsoft 365
- Exchange Online PowerShell Module – Install Here
- Confirm if any User, Device or 3rd Party Application Is using Legacy Authentication. For Scan to Email Functions please see the following guide from Microsoft Option 3.
Block Legacy Protocols & Disable Basic Authentication
1. Open PowerShell and run Connect-ExchangeOnline 
2. Login with Microsoft 365 Global Admin Account. 
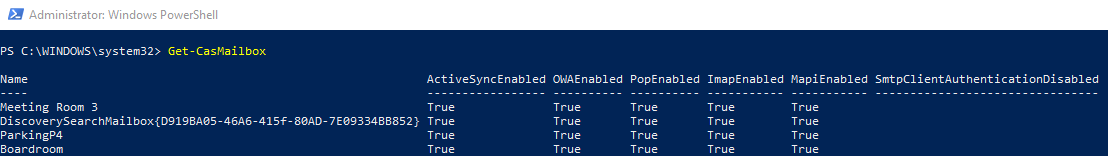
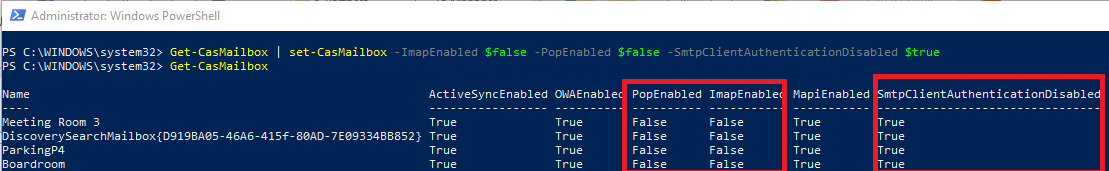
3. Verify all listed mailboxes with SMTP/IMAP/POP enabled. Run the below command:
Get-CasMailbox
4. Run the command to disable IMAP/POP/SMTP for all mailboxes.
Get-CasMailbox | set-CasMailbox -ImapEnabled $false -PopEnabled $false -SmtpClientAuthenticationDisabled $true
Run another command below to verify:
Get-CasMailbox
5. If you wish to disable legacy protocols per user, use the below command instead. Otherwise, skip this step.
Set-CASMailbox -Identity name@domain.com -ImapEnabled $false -PopEnabled $false -SmtpClientAuthenticationDisabled $true
6. Disable POP and IMAP upon new mailbox creation run the below command.
Get-CASMailboxPlan | set-CASMailboxPlan -PopEnabled $false -ImapEnabled $false
7. Configure an Authentication Policy in Microsoft 365 to block Basic Authentication. This will block access at the pre-authentication level. This protects against login request coming through legacy end-points.
With your active PowerShell session run the below commands in order. (wait for each to complete)
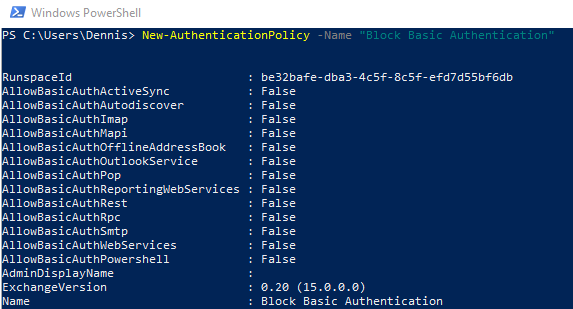
New-AuthenticationPolicy -Name “Block Basic Authentication”
This will create the Authentication Policy in Microsoft 365.
Set-OrganizationConfig -DefaultAuthenticationPolicy “Block Basic Authentication”
This will set the policy for all new user accounts that are created in the future.
Get-User | Set-User -AuthenticationPolicy “Block Basic Authentication”
This will set the policy for all existing accounts. (takes 24hrs to take affect)
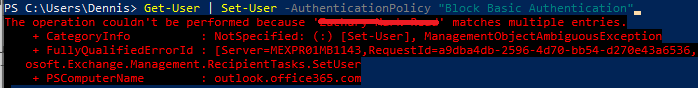
If you receive the above duplicate issue, run the command below:
$Users = Get-User
ForEach($User in $Users)
{
Set-User -Identity $User.GUID.Guid -AuthenticationPolicy “Block Basic Authentication”
}
Note: You will be prompted to confirm the next action, press A each time until you are no longer prompted. Legacy Protocols and Basic Authentication is now successfully Disabled.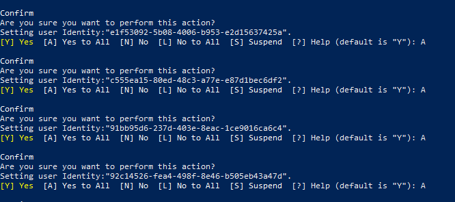
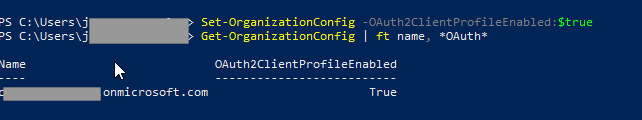
8. Verify if Modern Authentication is Enabled, run the following command in PowerShell:
Get-OrganizationConfig | ft name, *OAuth*
If the result is False, run the command below to turn it on:
Set-OrganizationConfig -OAuth2ClientProfileEnabled:$true