Purpose
When applications need to request fresh authentication from Microsoft Entra ID, meaning they need Entra ID to re-authenticate the user even if the user has already been authenticated, they can send the prompt=login parameter as part of the authentication request.
When this request involves a federated user, Microsoft Entra ID must inform the identity provider (IdP), such as AD FS or Practice Protect, that the request is for a fresh authentication.
Consider a situation where your users are federated via Practice Protect and are being continuously prompted for login in Microsoft 365 apps like Outlook, Teams, and others — even after entering the correct credentials.
This article will guide you on how to set the PromptLoginBehaviorto disabledin Microsoft 365. This configuration ensures that only wfresh=0 is sent to AD FS. As a result, it should help resolve the persistent login prompts experienced by users.
Prerequisite
- Global Admin Access in the Microsoft 365 Tenant
- Microsoft Graph PowerShell Module. You can install it here.
Instruction
- Run PowerShell and run the command below
Connect-MgGraph -Scopes “Domain.Read.All”, “Domain.ReadWrite.All”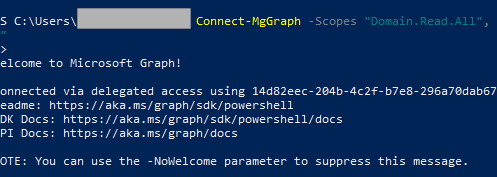
- Authenticate with a Microsoft 365 Admin Account. This connects you to Microsoft Graph with the required permissions. Admin consent may be required.
- Run the command below to retrieve domain federation settings. Note: Replace yourdomain.com with your actual domain name.
Get-MgDomainFederationConfiguration -DomainId “yourdomain.com”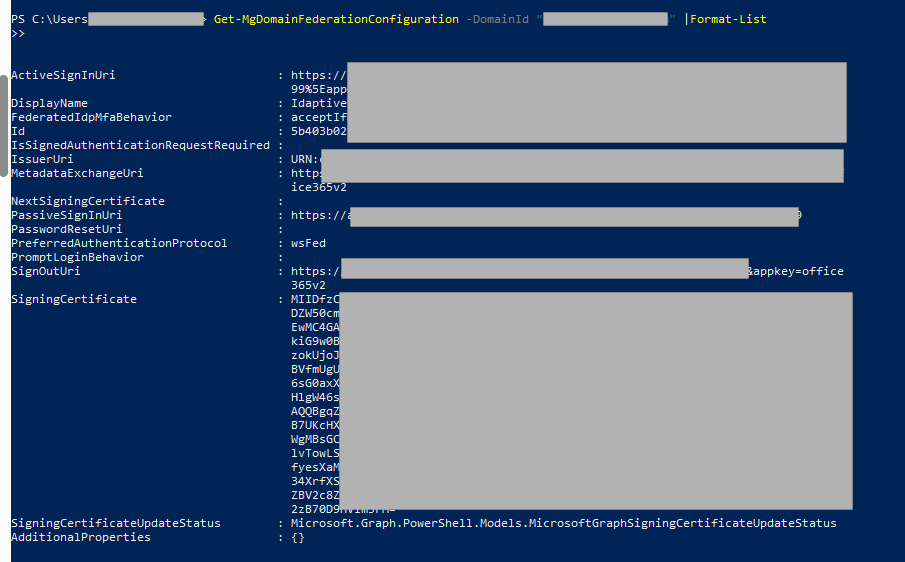
- Run the command below to trust MFA performed by the federated IdP and will not prompt the user again for MFA. Note: Replace yourdomain.com with your actual domain name.
Update-MgDomain -DomainId “yourdomain.com” -BodyParameter @{ federatedIdpMfaBehavior = “acceptIfMfaDoneByFederatedIdp” }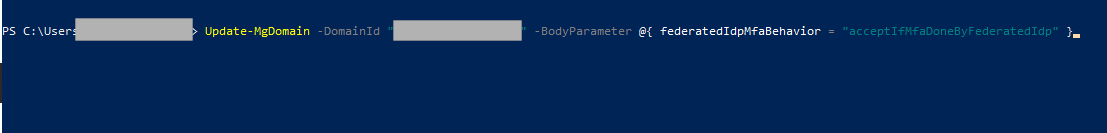
- Repeat for all Federated Domains.
