Overview
Microsoft is planning the deprecation of Basic Authentication for multiple protocols before its removal (Date TBC by Microsoft). Basic Authentication relies on sending usernames and passwords — often stored on or saved to the device — with every request, increasing the risk of attackers capturing users’ credentials, particularly if not TLS protected. Basic Authentication is unable to enforce MFA and is superseded by Modern Authentication.
Basic Authentication
Basic & legacy authentication mechanisms that rely solely on username and password. It has proven ineffective and is not recommended in modern IT environments especially when authentication is exposed to the internet as is the case for Microsoft 365.
Modern Authentication
To address the common security risks and user experience associated with Microsoft 365 deployments, Microsoft introduced the Active Directory Authentication Library (ADAL) for Office 365 client applications, referred to as Modern Authentication. Modern Authentication secures Microsoft 365 resources using multi-factor authentication, certificate-based authentication, and SAML-based logins (such as Federation), for a true single sign-on experience.
For MFA to be effective, you will need to block basic & legacy authentication. The reason behind this is legacy authentication protocols like POP, SMTP, IMAP, and MAPI cannot enforce MFA making them preferred entry points for adversaries attacking your organization…
The numbers on legacy authentication from an analysis of Microsoft Entra ID (formerly Azure Active Directory traffic are stark:
- More than 99 percent of password spray attacks use legacy authentication protocols
- More than 97 percent of credential-stuffing attacks use legacy authentication
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled
Older protocols like Exchange ActiveSync, EWS, and MAPI can also still be used with basic authentication overriding MFA/Modern Authentication. For example, Outlook clients can default to Basic Authentication by modifying the registry on Windows machines.
This complexity presents a major challenge in balancing support for email applications preferred by end-users and enforcing MFA across the entire Microsoft 365 environment. The “Expected Changes” section below addresses the trade-offs that must be made to enforce MFA for Microsoft 365.
Expected Changes
Before proceeding further, we should mention that the configuration changes listed in this document will enforce the following behaviors:
- All-access to Microsoft 365 will be over Modern Authentication.
- Clients that rely on legacy authentication protocols (including but not limited to, SMTP, POP, IMAP, ActiveSync Basic, and MAPI Basic) will be prevented from accessing Microsoft 365 and will be required to reauthenticate with Modern Authentication.
- Clients that don’t support modern authentication will no longer be allowed to access Microsoft 365 over basic authentication.
- Microsoft 365 Administrators will need the Modern Authentication-supported PowerShell module to connect to online Exchange.
-
Some 3rd Party Integrations still require basic authentication as they are still working on their migrations to Modern Authentication. In this instance, there will be no option but to enable basic authentication on a per-user/account basis. (See instructions below on Dealing with Exceptions)
Identifying Use of Basic & Legacy Authentication
The following guide will show you how to identify, use, and plan for the changes required.
Failed login attempts from strange locations/IPs in the logs would indicate ongoing brute force and spray attacks against the Microsoft 365 tenant.
Note: Certain 3rd Party Systems like CCH, SuiteFiles, and OnePractice are still using Basic Authentication, if you notice these accounts in your logs take note of the account in use to create an exception.
- Log in to the Microsoft Entra ID with an Administrator Account.
- On the left menu, click Sign-in Logs under Monitoring & Health
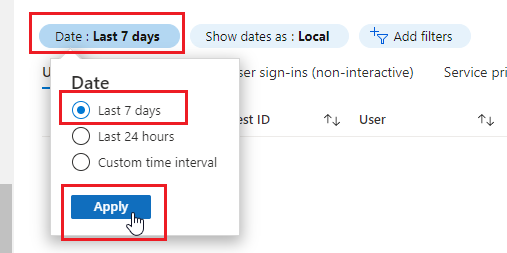
- Click the Date filter then select 7 Days. Click Apply.
- Click Add filters. Chose Client App then click Apply.
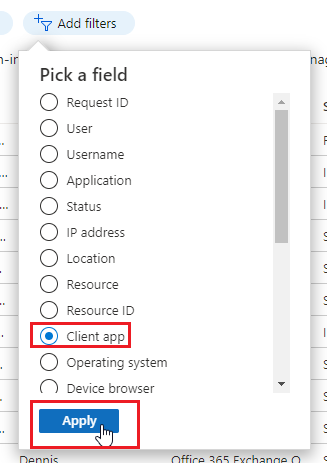
- Click the Client app filter.
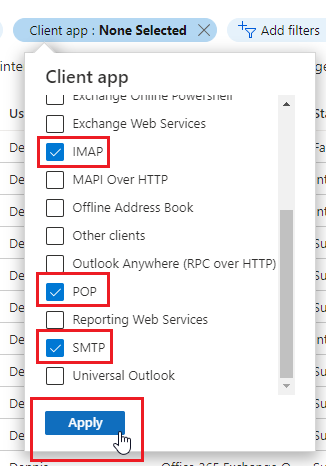
- Select IMAP, POP, and SMTP then click Apply.
- This will now display the last 7 days of logs where Legacy Protocols (SMTP, POP, IMAP) were used if any. Click any log entry for more details. The log entry will show which account and what protocol was used.
Note: The typical use of legacy protocol is Scan to Email from an office scanner or printer)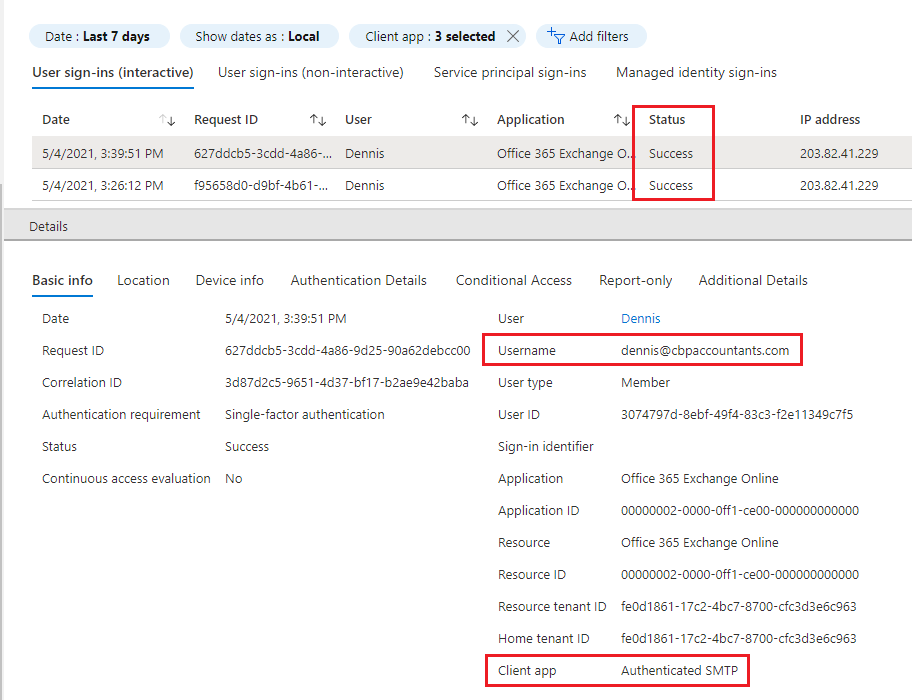
- Filter the log for Legacy Authentication Use.
Click on Client App and select everything listed used Legacy Authentication Clients excluding SMTP, POP, and IMAP, and click Apply.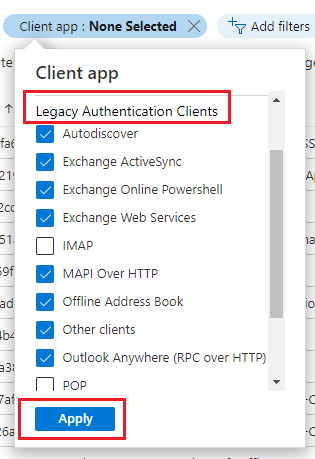
- This will now display the last 7 days of logs where Legacy Authentication was used. The most common are ActiveSync and MAPI over HTTP. This indicates that users have Outlook or Phones connected without Modern Authentication (No MFA).
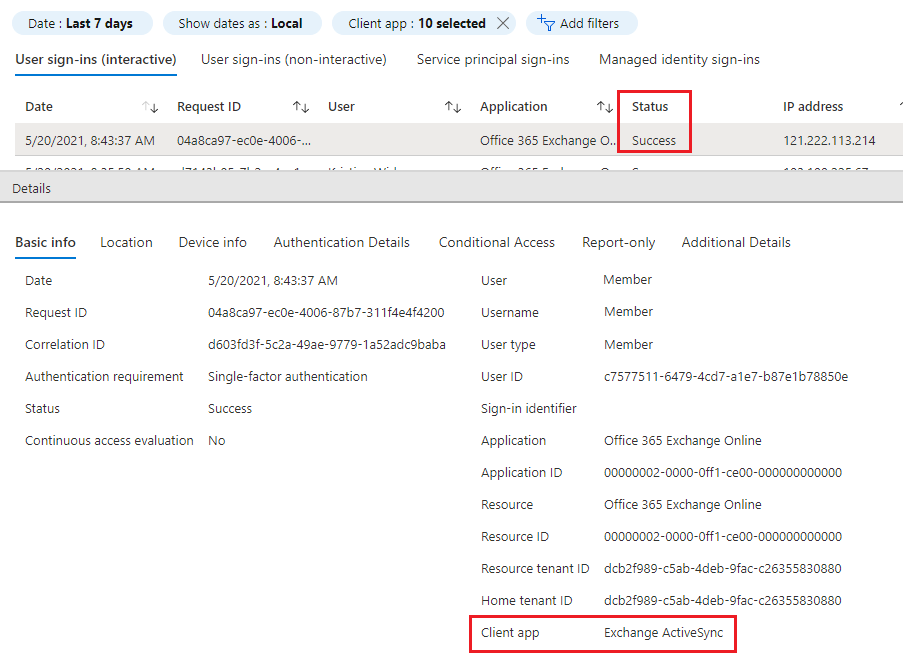
- List down the User accounts using Basic Authentication to prepare the users for Modern Authentication.
- List down any 3rd party Service accounts using Basic Authentication. Eg SuiteFiles
Scan to Email (SMTP)
If you have identified that SMTP is in use in the above steps (Step 8) and if required going forward there are three main options below for moving this off Office 365 Basic Authentication. Below are in order of preference:
- Configure Email connector in Microsoft 365 for SMTP Relay. Please see Option 3 Guide from Microsoft here for setup instructions. Requires an external Static IP behind the device/system sending emails.
- Scan to Email only required and behind Dynamic IP. If the only requirement is scan to email and the printer only support basic authentication and only a few emails are sent. You can look to use the SMTP Server of your ISP provider, we would advise to also change the send from address to your ISP email account to avoid any Spam/SPF issues.
- If System/Device requires Basic Authentication, then setting up a Secure SendGrid account via Microsoft 365/Entra ID is a good option. See Microsoft’s documentation here. You may also create an account directly at SendGrid.com.
Create a Microsoft 365 Authentication Policy to Block Basic Authentication
- Open PowerShell and run Connect-ExchangeOnline
- Login Box will appear. Login with Microsoft 365 Global Admin Account.
- You are now connected.
-
Run New-AuthenticationPolicy -Name “Block Basic Authentication”
This will create the Authentication Policy in Microsoft 365.
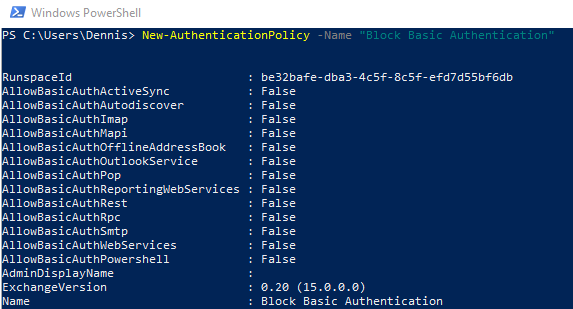
- Run Set-OrganizationConfig -DefaultAuthenticationPolicy “Block Basic Authentication”
This will set the policy for all new user accounts that are created in the future.
- Run Get-User | Set-User -AuthenticationPolicy “Block Basic Authentication”
This will set the policy for all existing accounts. (takes 24hrs to take affect)
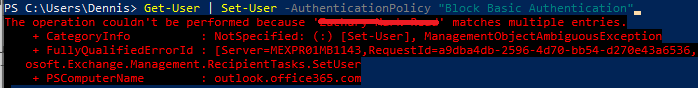
If you receive the above duplicate issue. You can run the below command instead:
$Users = Get-User
ForEach($User in $Users)
{
Set-User -Identity $User.GUID.Guid -AuthenticationPolicy “Block Basic Authentication”
} - Now verify if Modern Authentication is Enabled by Default on the tenant.
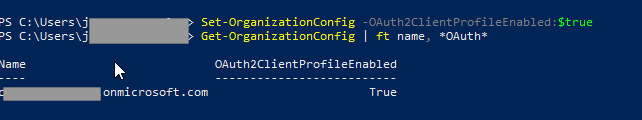
Run the following:
Get-OrganizationConfig | ft name, *OAuth*
If the result is False, run the command below instead:
Set-OrganizationConfig -OAuth2ClientProfileEnabled:$true
Disable Legacy Protocols on Mailboxes
- Open PowerShell and run Connect-ExchangeOnline

- Login Box will appear. Login with Microsoft 365 Global Admin Account.

- You are now connected.
-
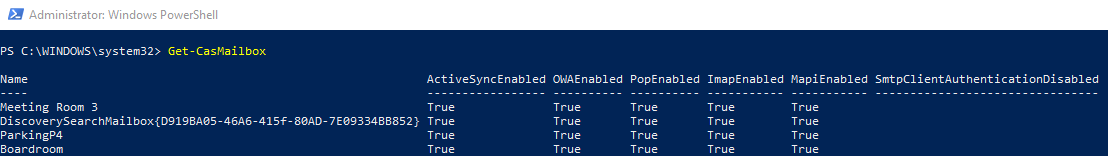
Verify list of Mailboxes with SMTP/IMAP/POP enabled. By default they are enabled. Run the below command.
Get-CasMailbox
- Run the following command to disable IMAP/POP/SMTP for all Mailboxes.
Get-CasMailbox | set-CasMailbox -ImapEnabled $false -PopEnabled $false -SmtpClientAuthenticationDisabled $true
Then Get-CasMailbox to verify
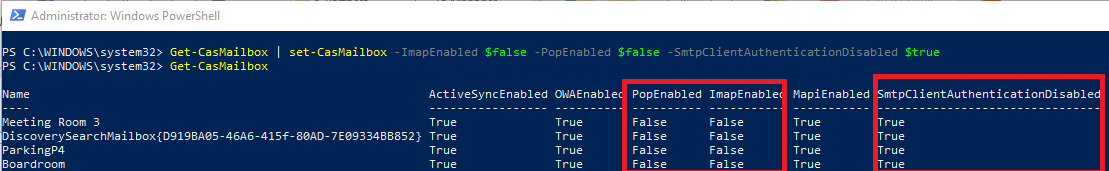
- If you receive a duplicate issue you can use the below command to run again.
$Users = Get-CasMailbox
ForEach($User in $Users)
{
set-CasMailbox $User.GUID.Guid -ImapEnabled $false -PopEnabled $false -SmtpClientAuthenticationDisabled $true
} - To disable POP and IMAP upon new mailbox creation run the below command. Get-CASMailboxPlan | set-CASMailboxPlan -PopEnabled $false -ImapEnabled $false
Dealing with Exceptions
Whenever possible, you want to avoid unlocking Basic Authentication. However, there are certain third parties that are still working on their migrations to Modern Authentication. You can enable Basic Authentication on a per user/account basis with the below commands:
- Open PowerShell and run Connect-ExchangeOnline

- Login Box will appear. Login with Office 365 Global Admin Account.

- You are now connected.
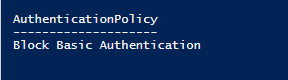
- Confirm the Block Basic Policy is running on that account. Get-User -Identity SuiteServiceAccount@companydomain.com | select AuthenticationPolicy
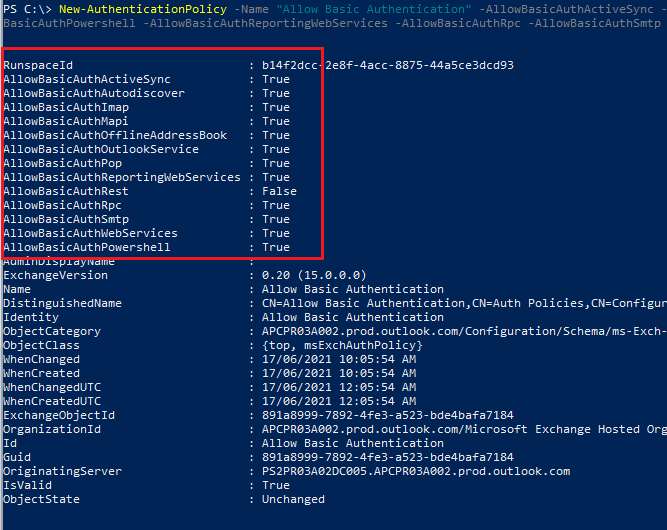
- Now create an “Allow Basic Authentication” Policy with the below command. This can be modified to the Basic Authentication Services you require: New-AuthenticationPolicy -Name “Allow Basic Authentication” -AllowBasicAuthActiveSync -AllowBasicAuthAutodiscover -AllowBasicAuthImap -AllowBasicAuthMapi -AllowBasicAuthOfflineAddressBook -AllowBasicAuthOutlookService -AllowBasicAuthPop -AllowBasicAuthPowershell -AllowBasicAuthReportingWebServices -AllowBasicAuthRpc -AllowBasicAuthSmtp -AllowBasicAuthWebServices .
- Now run run the following command to apply the new Allow Policy to the account required: Set-User -Identity SuiteServiceAccount@companydomain.com -AuthenticationPolicy “Allow Basic Authentication”
- This is only applied to that account and all other accounts will still be blocked as default.
- In rare instances you may also have to change the Default Policy to Null if you encounter issues after setting a service user to Null. We have not seen this with accounting applications. If you encounter this you may run the following command to test. Set-OrganizationConfig -DefaultAuthenticationPolicy $Null . This will not change the status of the accounts where the block policy was directly set and should be avoid where possible.
Note that the authentication policies assigned to users take precedence over the default policy.
Troubleshooting Outlook & Phone Authentication
Once Basic Authentication is blocked any device/system still using basic will require to re-authenticate.
Phones:
User can end up in a prompt loop if the Phone was using ActiveSync with Basic Authentication. In order to switch the Phone over to Modern Authentication, the email account needs to be removed from the Phone and re-added. When it is re-added the phone will detected to use Modern Authentication and prompt for MFA.
Outlook/Office:
Confirm computers are all using Office 2013+. Office 2010 is EOL and doesn’t support Modern Authentication.
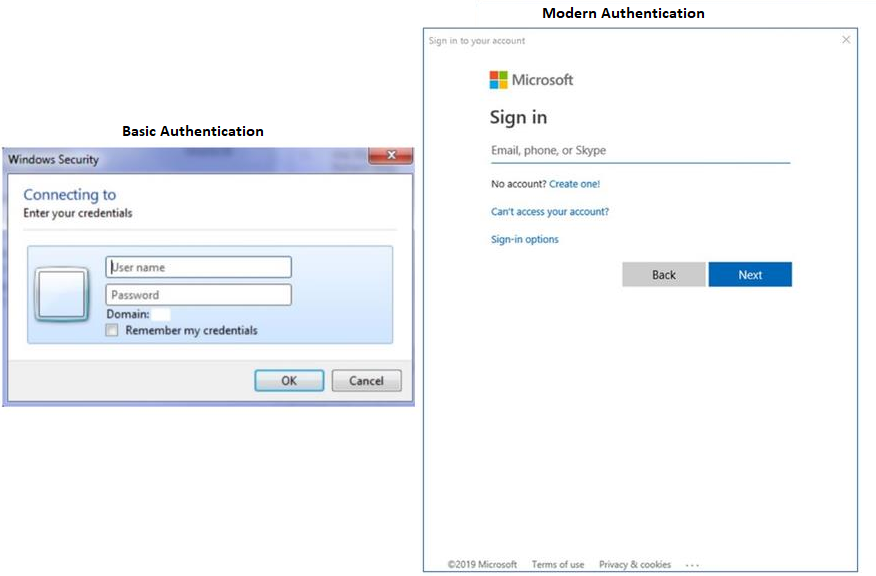
Below is an example of a Basic and Modern Authentication Prompt, if you are still receiving Basic Prompt after disabling you may need to investigate.
In most cases you do not need to re-profile Outlook, but clear the saved Basic Authentication Settings.
- Close Outlook
- Go to Control Panel then Credential Manager
- Go to Windows Credentials
- Remove any saved Credentials that relate to the Email/Outlook account.
- Reopen Outlook, if you are still not prompted for Modern Authentication – continue the below steps
- Check for the following registry keys:
16.0 for Office 2016 and 15.0 for Office 2013
[HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Identity “EnableADAL”=dword:00000001
If EnableADAL is set to 0 change this to 1. If the Key doesn’t exist create a DWORD with Value 1
Retest Outlook – If still not prompting you can set the following two keys to enforce Modern Authentication.
[HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Identity “DisableADALatopWAMOverride”=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Identity “DisableAADWAM”=dword:00000001
-
Reboot the Computer if still having issues with Modern Authentication.
- If after Reboot you are still being prompted with Basic Authentication, remove any old saved Basic Identities in the Registry. These can be found here: HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Identity\Identities
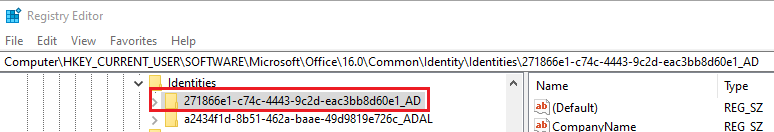 Look for any Identity Keys with “AD” appended at the end and remove. This should cause a reauthentication in Outlook and doesn’t remove the Email Profile. Do not remove any keys already showing “ADAL” which is Modern Authentication.
Look for any Identity Keys with “AD” appended at the end and remove. This should cause a reauthentication in Outlook and doesn’t remove the Email Profile. Do not remove any keys already showing “ADAL” which is Modern Authentication.
