Overview
If you are using Microsoft Entra ID (formerly Azure Active Directory) to store and manage your user information, you can configure Practice Protect Identity to recognize it as a directory service and see the users as managed domain users. You can then add your Entra ID users to roles and grant permissions to access applications. Your users can then log in to Practice Protect Identity with their Entra ID accounts and launch assigned applications.
Considerations
In this deployment method, the core attributes of the user accounts are controlled in Entra ID/Microsoft 365 including passwords. As EntraID is the point of truth, we are also unable to implement Email Integration (Federation) in this deployment as it would cause an authentication loop. That’s why it is recommended that this deployment method is only done in an instance where your Microsoft Entra ID is managed by an IT professional. You have either Microsoft Entra ID Security Defaults Enabled or Microsoft Entra ID Conditional Access Configured with GEO Blocking.
Migration
If you have a current deployment of Practice Protect and would like to switch over to Microsoft Entra ID as the Source Identity, please reach out to the support team to plan a migration. As each source directory creates its user source and existing user accounts cannot be linked to new directories, incorrect migration can lead to duplicate accounts.
You may reach out to our support team at [email protected]
Instructions
Register an application in Entra
- Login to Microsoft Entra Admin Center with an Administrator Account. (Note this is the same Administrator Account as Microsoft 365)
- On the left menu, go to Applications and click App Registrations.
- Click New Registration.
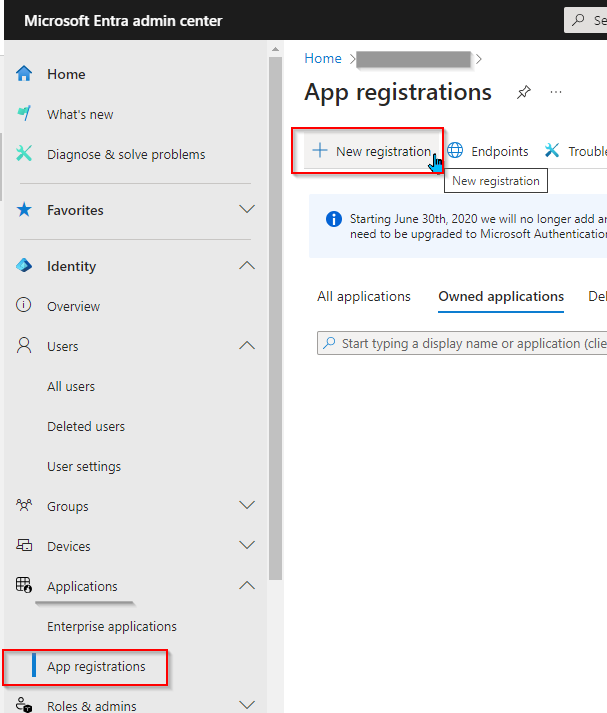
- Set the Name to Practice Protect leave all other settings default and click Register.
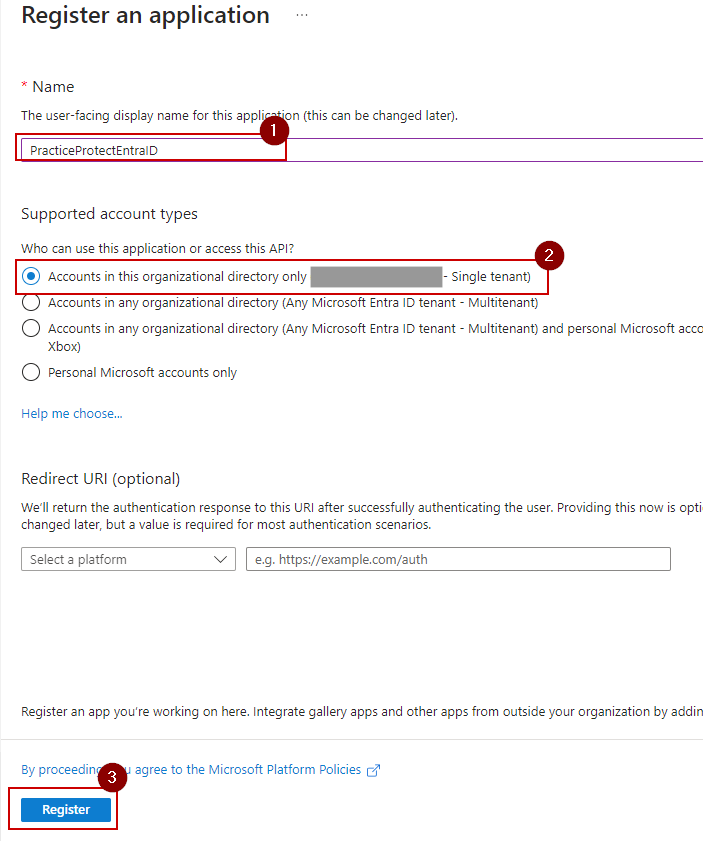
- Go to API permissions, then click Add a permission.
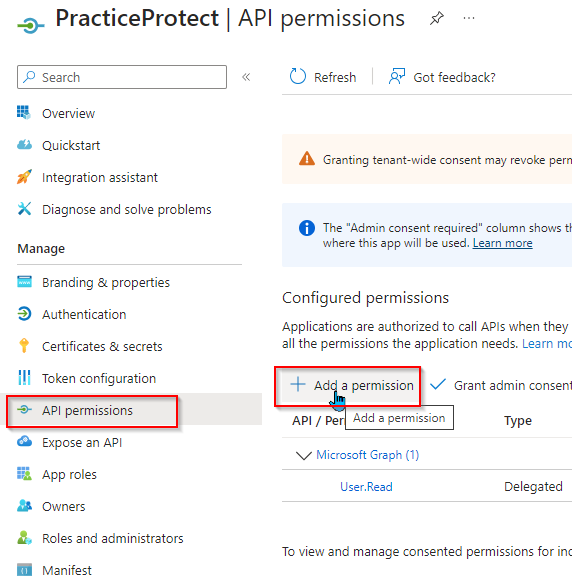
- Click Microsoft Graph
- Click Application permissions.
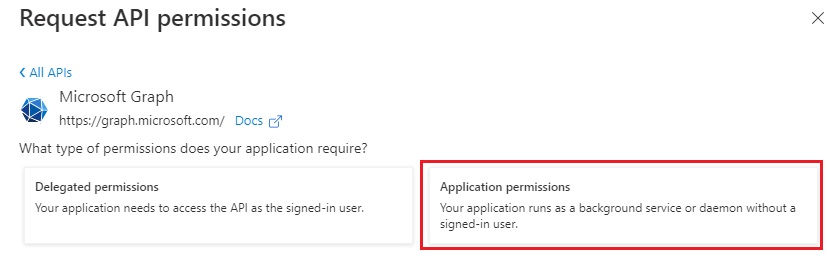
-
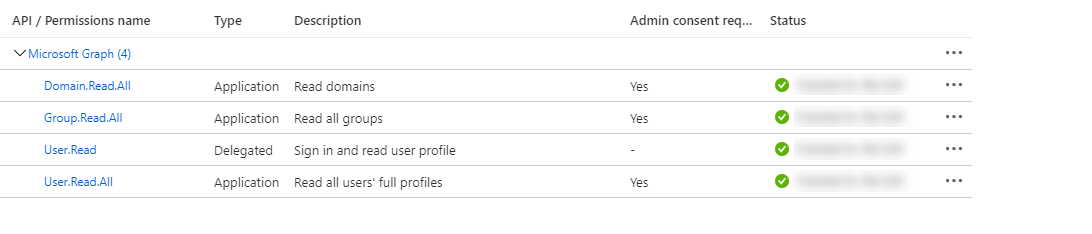
Select the following permissions below. The Type should be Application then click Add permissions.
- Domain.Read.All
- Group.Read.All
- User.Read.All
- Click Grant admin consent for <your company>.
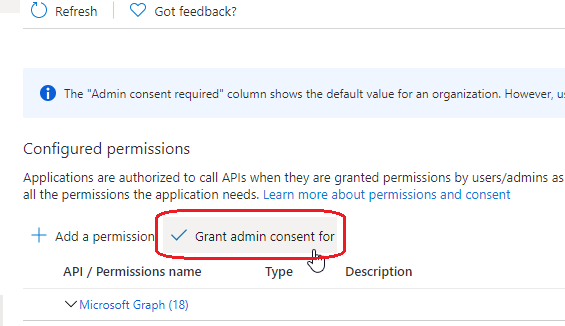
- Click Yes on the confirmation prompt.
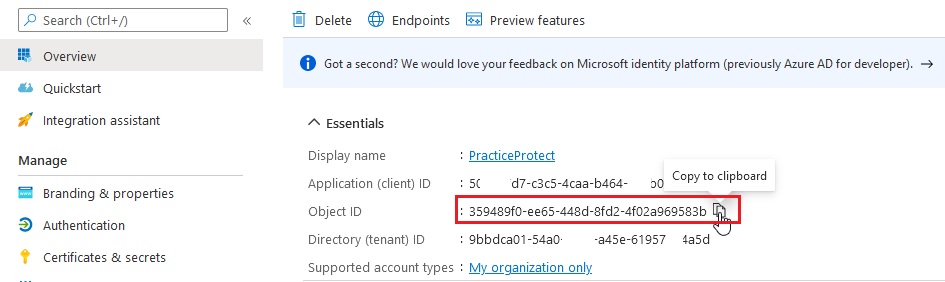
- Return to the overview of the created app (i.e. PracticeProtect). Next to ObjectID click copy.
- Open PowerShell. Run the following commands to connect to AzureAD and Set the Date Variables.
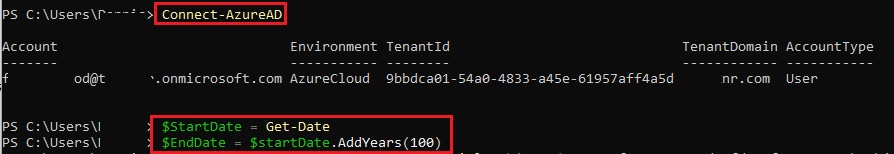
Then run the following command to generate a secret.
Note – change the ObjectID value to the Object ID you copied from Step 3
New-AzureADApplicationPasswordCredential -ObjectId 359489f0-ee65-448d-8fd2-4f02a969583b -StartDate $startDate -EndDate $endDate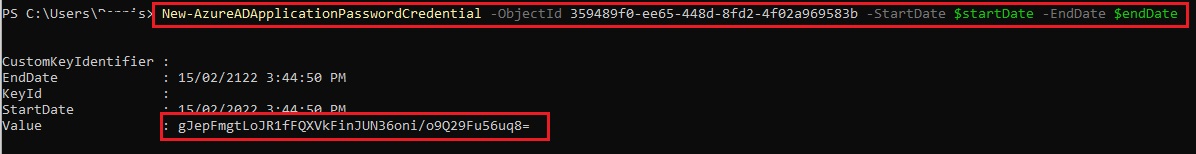
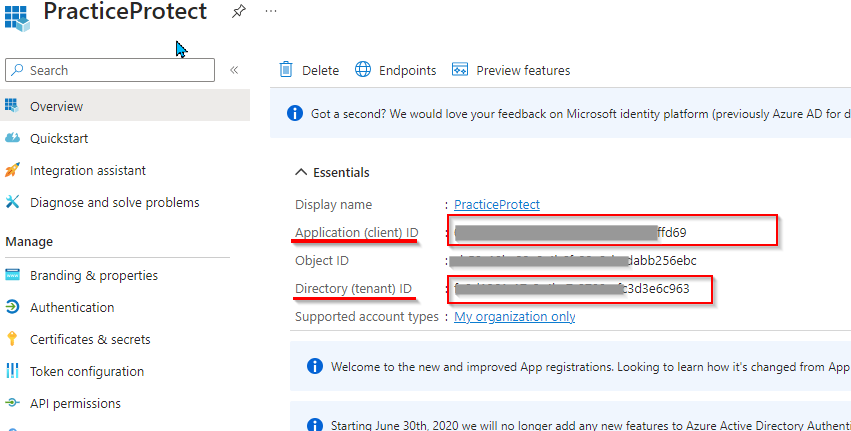
Important! Copy the Value Output to your clipboard/notepad. This is needed in the next steps as if you missed it, you will have to generate it again. - Return to the Microsoft Entra Admin Center then go to the Overview page of the app you registered (E.g. PracticeProtect) and copy the following values:
- Application (client) ID
- Directory (tenant) ID
Add the Microsoft Entra ID Directory in the Admin Portal
- Open a new browser tab and log in to the Practice Protect Admin Portal
- Go to Settings > Users > Directory Services, then click Add Microsoft Entra ID.
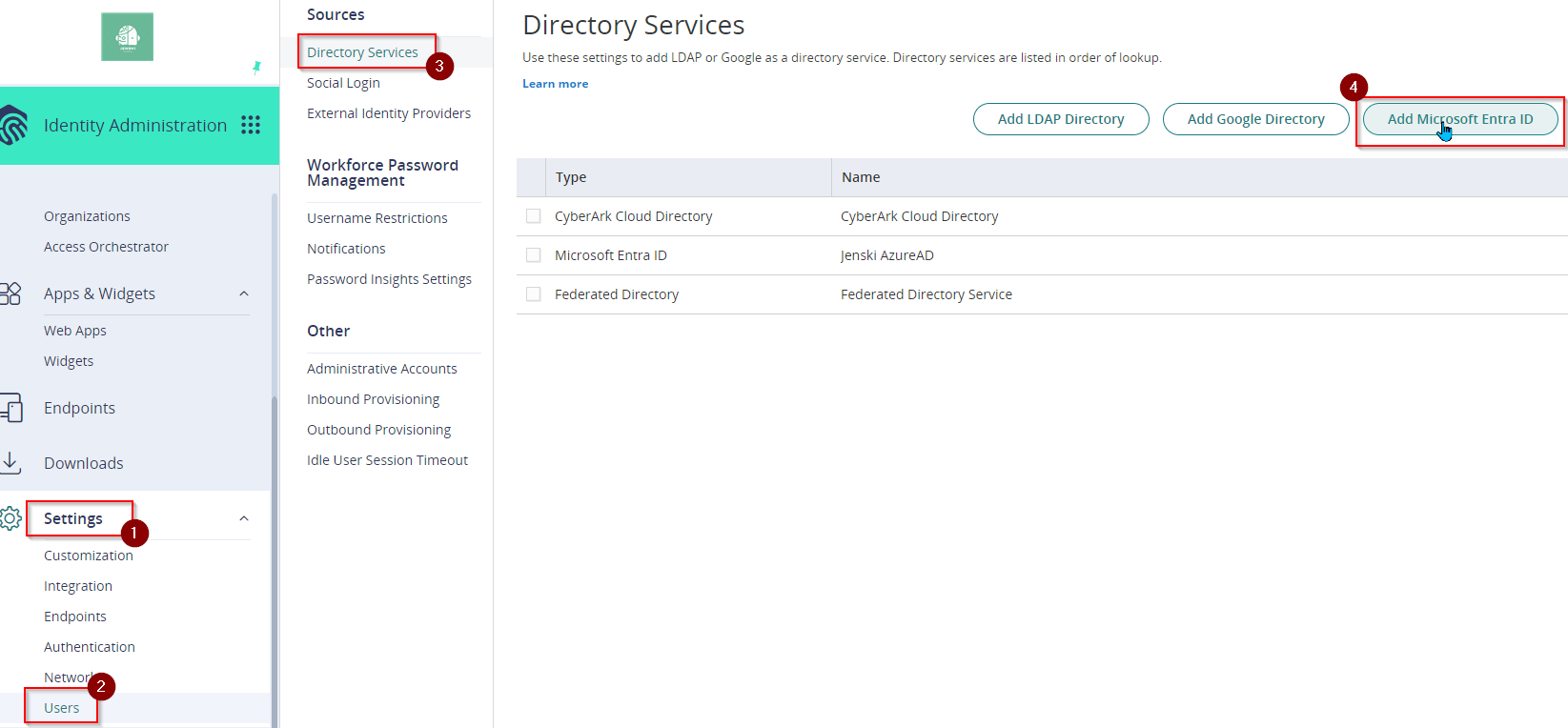
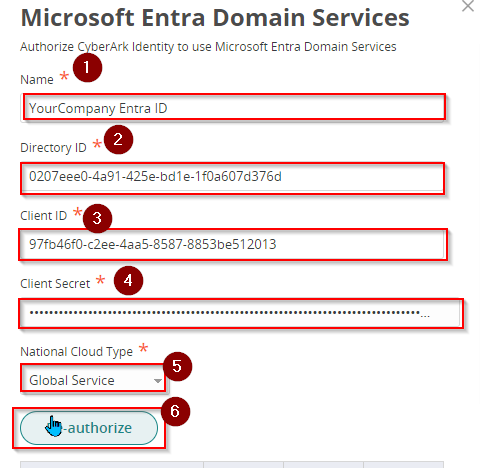
- On the Microsoft Entra Domain Sevices form, enter a Name for your Directory. (e.g. YourCompany Entra ID).
- Paste the Directory ID and Client ID you copied from Step 5 on the Register an Application in Entra section in the required fields.
- Also, paste the Client Secret you copied from Step 4 on the Register an Application in Entra section.
- Set National Cloud Type to Global Service
- Click Authorize.
Your available domains appear in the table below the authorize button. Domains not indicated as Federated are considered Managed domains.
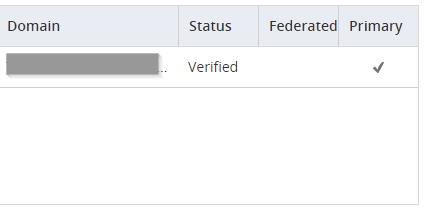
If you add additional custom domains in Microsoft Entra ID, you have to re-authorize it in the Admin Portal before you can query the users and groups.
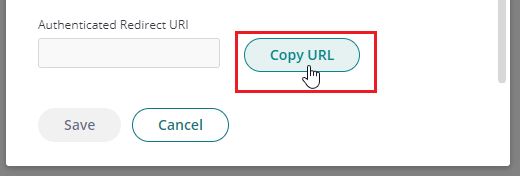
- Below the list of domains, click Copy URI to copy the authenticated redirect URI.
- Go back to the Microsoft Entra ID page > Overview of your registered app (e.g. PracticeProtect) and click Add a Redirect URI.
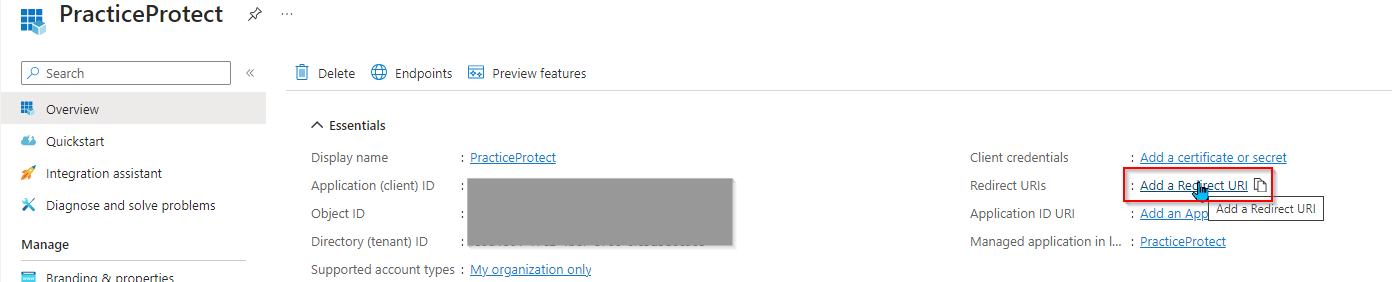
- Click Add a platform, then click Web.
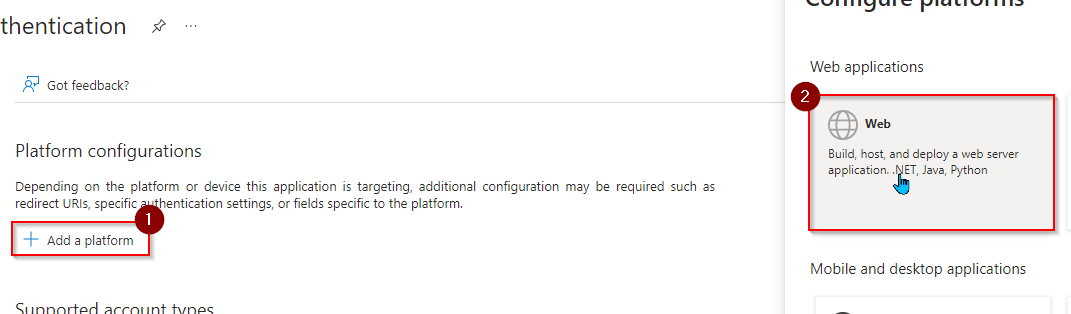
- Paste the Redirect URI you copied from Step 8 into the Redirect URIs field.
- Select ID tokens (used for Implicit and hybrid flows), then click Configure.
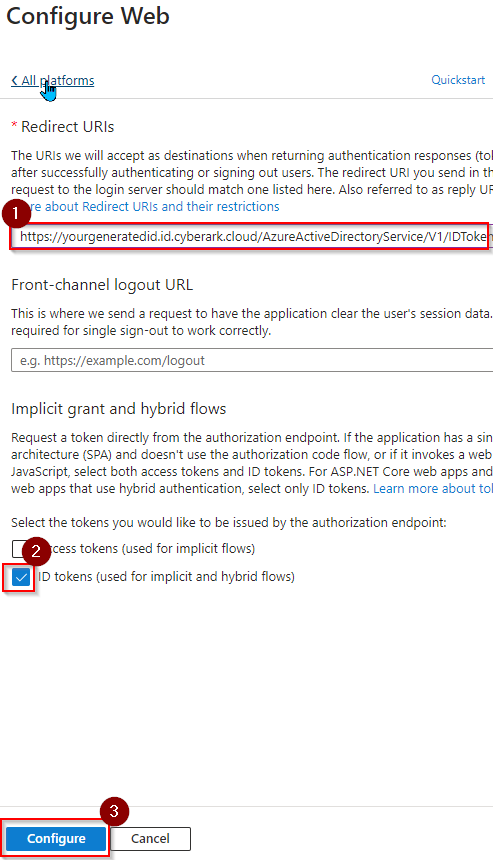
- click Save. PracticeProtect app with the redirect URI is now set up.
-
The Microsoft Entra ID users can now log in to Practice Protect via their Microsoft 365/Entra ID credentials.
You can also utilize the Microsoft Security group and add them to Practice Protect roles to grant user application permissions, and security policies or enforce authentication profiles. -
On the login page of Practice Protect, enter your Microsoft 365/Entra ID username and click Next.
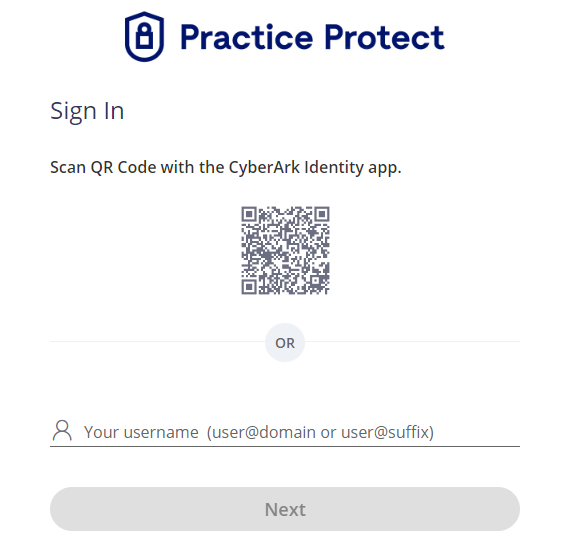
-
Users will be redirected to Microsoft 365 login for login authentication. Note: If your Microsoft 365 Tenant has a Conditional Access Policy applied like MFA enforcement, this will prompt users to authenticate their sign-in.
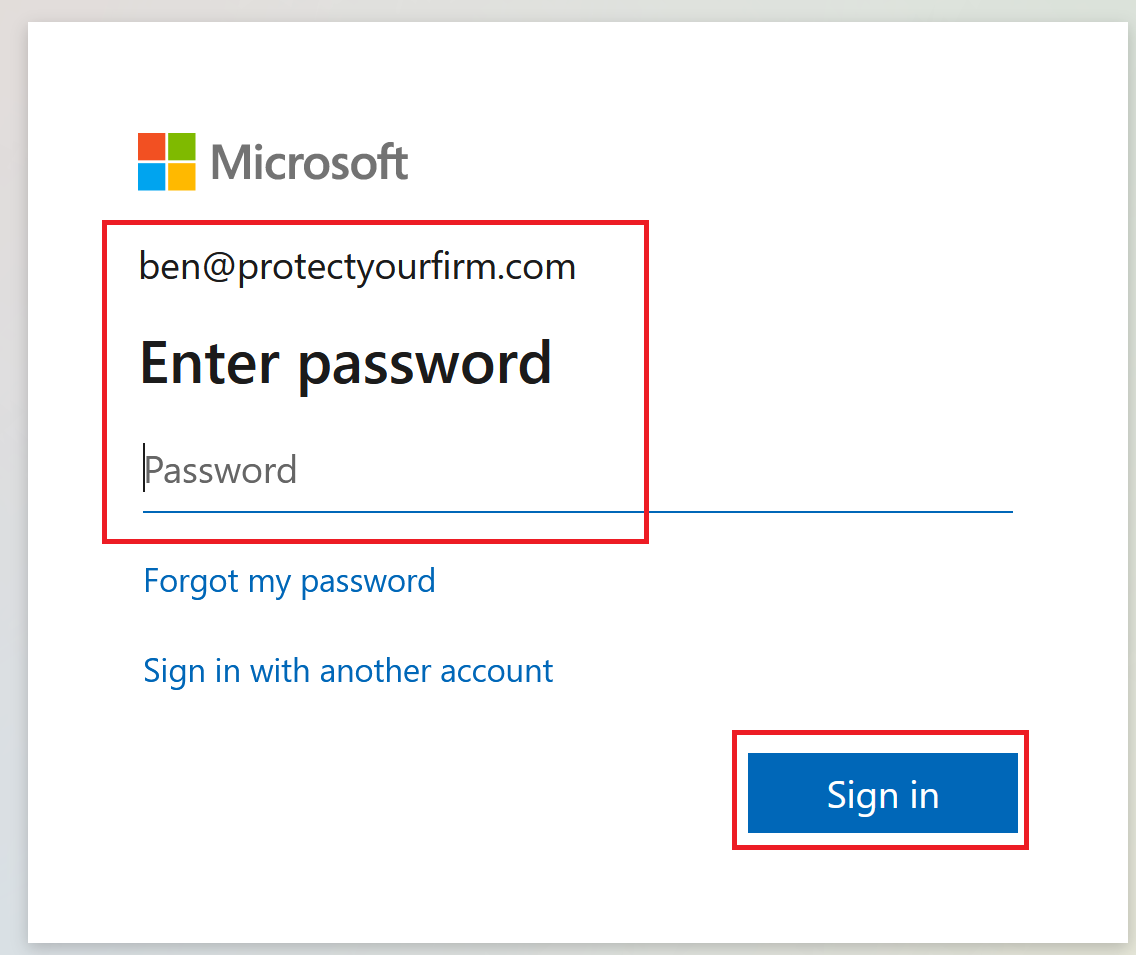
-
Once authenticated, Users now have access to the User Portal of Practice Protect.

