- Email is the most commonly breached component of an accounting app stack due to the sensitive nature of stored correspondence and the ability to send infected emails to your contacts.
- Public cloud email and cloud file storage vendors are geared towards login convenience to increase market share leaving security as the responsibility of the subscribing entity in the license agreement you’ve accepted.
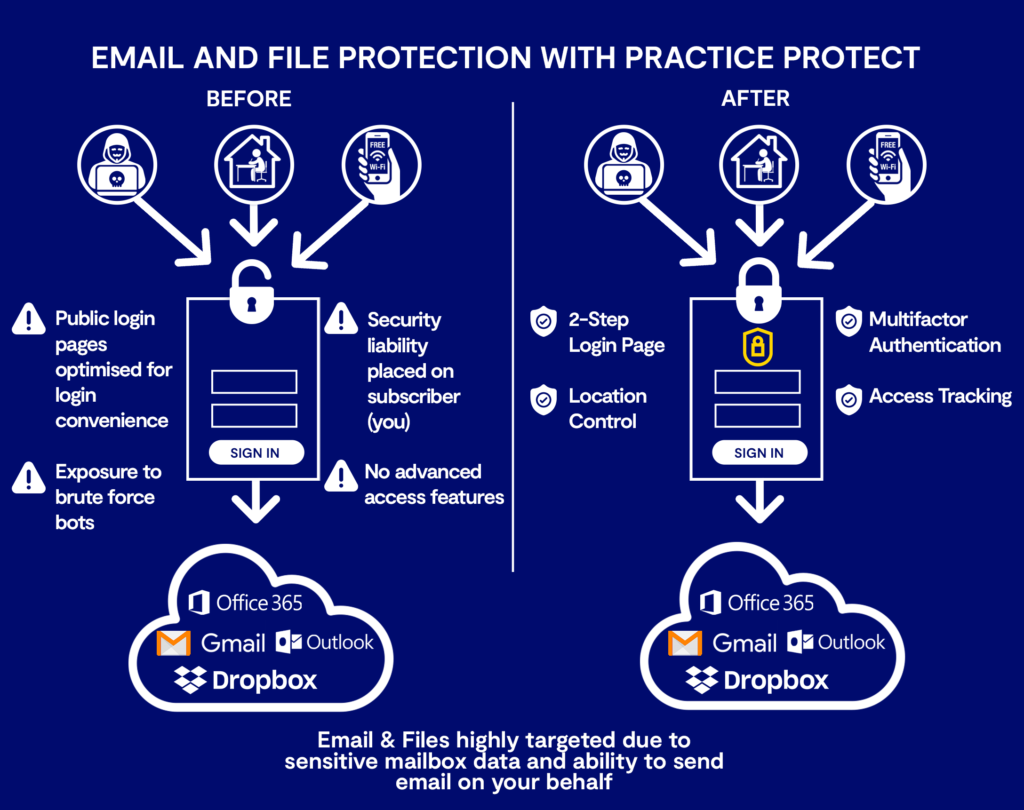
- Applying email and cloud file protection allows accounting firms to integrate robust security features such as location control, access tracking and two factor authentication over sensitive emails and files.
- Email integration is applied during on-boarding via a technical integration at the back end and makes no difference to the user experience. When applied, users login via their Practice Protect credentials and then is required to meet the policy requirements set by the client.
Email & Cloud File Integration Explained
Why Email and Cloud File Integration?
Email mailboxes are the most highly valued target from a criminal’s perspective. Illegal access to an accountant’s mailbox grants access to years of sensitive communication and the ability to leverage professional trusted relationships by sending unsolicited infected emails to contacts.
Mailboxes are less secure than other accounting apps due to the fact that global cloud email providers are in a war for market share with convenience being their weapon of choice. The responsibility for security is pushed on the subscribing entity in the end user license agreement.
How does it work?
Email & Cloud File Integration aka “Federation ADFS”, “SAML” or “OpenID” is used to integrate Practice Protect accounts with the accounts of cloud applications such as Office 365, Google Mail, Dropbox, FYI Docs, and Suite files.
The purpose is to extend the security controls that Practice Protect has like location control, multi-factor authentication, user logging etc to protect your company files and email stored in cloud-based applications.
What happens when it is enabled?
When integration is applied to your email or cloud storage, your login method will stay the same. The only change will be that your login will now be your Practice Protect Account instead of your normal username/password.
See how the process looks for yourself below:
How does this change the way we administer our Email Accounts?
Once Email or Cloud File Integration is enabled for service. The primary account becomes the Practice Protect account and the application account becomes a linked account.
This will change the way your IT Administrator creates and removes accounts. Primarily with your Email provider (Office 365 & Google Workspace).
As the Practice Protect account becomes the “point of truth” certain account attributes have to now be administered from Practice Protect. Below is a list of attributes affected and guides for your IT Administrator to adapt for a smooth transition to Email Protection.
Unless you are using the AzureAD Connector from Local Active Directory to Office 365, the below attributes will now be controlled by Practice Protect:
Office 365
Practice Protect Controlled/Synced Attributes:
- Primary Email/Username
- Display Name
- Immutable ID
- License Assignment (Optional)
Office 365 Controlled Attributes:
- Proxy Addresses (Excluding Primary Username/Email)
- Display Name, Title, Phone Numbers and other Contact Details of the Office 365 account.
- Hide From Address Book
- License Assignment
Detailed guides for your IT Administrator to adapt to your current internal user processes:
Google Workspace (formerly G-Suite)
Google Workspace Attributes and items are now controlled by Practice Protect:
- Display Name
- Primary Email/Username
- Email Alias (optional)
Detailed guides for your IT Administrator to adapt to your current internal user processes:
We would advise to share this information with your IT Administrator or external IT provider in order to facilitate a smooth update of these processes.
